Ecommerce
How is Symbolic Jewelry Timeless?

Symbolic jewelry has been a part of human culture for thousands of years. From ancient times to the present day, people have worn jewelry as a way to express their beliefs, values, and identity. Symbolic jewelry is not only beautiful but also carries a deeper meaning that connects the wearer to their culture, religion, or personal beliefs.
We reached out to Rachel Brown, the founder and designer of ONE LOVE jewelry designs which is bespoke symbolic jewelry. In an effort to connect with people and their values on a global scale, the jewelry designer has been making symbolic pieces for a while. In Brown’s collection, you can see a representation of the inclusivity and diversity of race, religion, sexual orientation, and culture.
Symbolic jewelry can be seen in almost every culture, from the intricate beaded necklaces of African tribes to the elaborate gold earrings of Indian brides. Each piece of jewelry is unique and carries a symbolic meaning that reflects the culture and beliefs of the wearer.
One of the earliest examples of symbolic jewelry is the ancient Egyptian amulet. Egyptians believed that amulets had magical powers that could protect them from evil and bring good luck. Amulets were often worn as jewelry, and each one represented a different aspect of Egyptian culture and religion. For example, the ankh symbolized life, the scarab beetle represented rebirth, and the Eye of Horus was a symbol of protection and power.
In many cultures, symbolic jewelry is also used as a way to communicate social status or rank. For example, in ancient Rome, gold rings were worn by senators and other high-ranking officials as a symbol of their status. In medieval Europe, jewelry was also used to indicate social status, with the nobility wearing elaborate gold and gemstone jewelry while commoners wore simpler pieces made from base metals.
Symbolic jewelry has also played an important role in religious practices. For example, in Christianity, the cross is a powerful symbol of faith and salvation. Cross necklaces and other jewelry are worn by Christians around the world as a way to express their faith and remind themselves of the sacrifice of Jesus Christ. Similarly, in Hinduism, the red dot on the forehead, known as a bindi, is a symbol of the third eye and spiritual enlightenment. It is commonly worn by women as a way to express their devotion to their religion.
In addition to expressing religious or cultural beliefs, symbolic jewelry can also be used as a way to express personal values and beliefs. For example, someone might wear a necklace with a tree of life symbol to represent their connection to nature, or a ring with an infinity symbol to represent the infinite nature of the universe. These pieces of jewelry not only have personal significance but also serve as a way to connect with others who share similar beliefs.
Symbolic jewelry can also be used as a way to commemorate important events or milestones in a person’s life. For example, a wedding ring is a symbol of the commitment between two people and is often passed down through generations as a family heirloom. Similarly, a graduation necklace or bracelet can be given as a gift to commemorate a significant achievement.
The importance of symbolic jewelry lies in its ability to connect us to our past, present, and future. It reminds us of our cultural and religious roots, our personal values and beliefs, and the important events and people in our lives. It is a way to express ourselves, to connect with others, and to carry a piece of our identity with us wherever we go.
In today’s world, symbolic jewelry continues to be an important part of our culture. In fact, it has become even more popular in recent years as people seek to express their individuality and connect with their heritage. The rise of handmade and artisanal jewelry has made it possible for people to find unique and meaningful pieces that reflect their personal style and values.
There are many different types of symbolic jewelry available today, from traditional pieces like cross necklaces and Celtic knot bracelets to more modern designs like minimalist geometric shapes and nature-inspired motifs. Some people even choose to create their own jewelry, using materials like clay, wire, and beads to create unique and meaningful pieces.
Artifiсiаl Intelligenсe
Beyond Passwords: Your Digital Self in the Age of Blockchain (Clickbait: Ditch Passwords Forever! This Tech Will Secure Your Online Life)

Beyond Passwords: Your Digital Self in the Age of Blockchain (Clickbait: Ditch Passwords Forever! This Tech Will Secure Your Online Life)
Tired of password Purgatory? Enter the Blockchain Oasis.
Remember that frantic morning scramble, brain aching for the elusive password to your bank account?
Or the sinking feeling when “incorrect password” flashes back, mocking your best guess?
We’ve all been there, prisoners of our own digital fortresses, locked out by the very keys meant to protect us. But what if we told you there’s a better way, a passwordless paradise called blockchain technology?
Think of it as your digital Swiss bank account, secure and impregnable.
Unlike the flimsy walls of traditional passwords, easily breached by hackers and cracked by brute force, blockchain builds fortresses with ironclad cryptography.
Your data, from medical records to online purchases, isn’t hoarded by corporations or vulnerable to centralized attacks.
Instead, it lives on a distributed ledger, a communal vault encrypted across thousands of computers, each one a guardian vigilantly watching over your digital self.
This isn’t just about convenience (though ditching those sticky notes is a major perk!). This is about ownership and control.
Blockchain empowers you to be the gatekeeper of your digital life. You decide what information you share, with whom, and for how long.
No more Big Brother data slurping or shady companies monetizing your privacy. You become the sovereign ruler of your own digital kingdom, wielding the keys to unlock or deny entry.
Imagine accessing your healthcare records without divulging them to every hospital you visit.
Picture transferring money across borders, instantly and securely, without banks taking a hefty cut.
Envision a world where your online identity isn’t a mosaic scattered across corporate servers, but a unified passport you carry with pride, granting access to services based on your own terms.
This is the promise of blockchain: a future where security isn’t a fragile wall of passwords, but a vibrant ecosystem of trust and empowerment.
Are you ready to leave Password Purgatory behind and step into the Blockchain Oasis? Buckle up, savvy internet user, because the revolution has just begun.
The Downside of Traditional Passwords
Why Are Passwords Failing Us?
In our digital age, passwords are the guardians of our online identities, yet they are failing us in more ways than one. Despite being the first line of defense in digital security, traditional passwords are increasingly becoming the weakest link. Let’s explore why.
The Illusion of Strength in Complexity
Think of the last time you created a password. Chances are, you were prompted to include a mix of letters, numbers, and symbols – the more complex, the better, right?
However, this complexity often leads to passwords that are hard to remember and, ironically, not as secure as we think. Cybersecurity experts have long debunked the myth that complexity equates to security.
In reality, it’s the length and unpredictability of passwords that matter most. But even then, no password is impervious to the sophisticated tactics employed by hackers today.
The Human Factor: Password Fatigue and Security Risks
As humans, we have our limits in remembering complex strings of characters. This leads to password fatigue – the tendency to reuse passwords across multiple accounts for convenience.
It’s like using the same key for your house, car, and office; if one gets lost or stolen, everything is compromised. This common practice significantly heightens the risk of mass data breaches.
Once a hacker cracks one password, they potentially gain access to an entire suite of an individual’s personal and professional digital life.
The Hacker’s Playground: Vulnerabilities in Password-Based Security
Hackers have a plethora of tools at their disposal to breach password-protected accounts. Techniques like brute force attacks, where automated software tries countless combinations until it finds the right one, are surprisingly effective against weak passwords.
Phishing attacks, where users are tricked into revealing their passwords, are increasingly sophisticated and difficult to spot.
Even when we think our passwords are safely stored, large-scale data breaches at major companies reveal that this is not always the case.
The Cost of Password Management and Recovery
The administrative burden of managing and recovering passwords is another often-overlooked downside.
For businesses, the cost of resetting passwords and dealing with security breaches can be astronomical.
For individuals, the time and effort spent managing passwords, coupled with the anxiety of keeping them safe, are a significant mental burden.
Biometric Authentication: A Step Forward but Not a Panacea
The advent of biometric authentication – using fingerprints, facial recognition, or retinal scans – seemed like a promising solution.
However, while biometrics offer convenience, they are not without their flaws. Biometric data, once compromised, cannot be changed like a password.
There are also privacy concerns and the potential for misuse of biometric data by corporations or governments.
Looking Beyond Passwords: The Need for a Paradigm Shift
The limitations of traditional passwords highlight the need for a paradigm shift in digital security.
We need a solution that is both secure and user-friendly, something that doesn’t require us to remember complex strings of characters or put our personal biometrics at risk.
This is where blockchain technology comes into play, offering a new way to authenticate identities and secure data without the pitfalls of traditional passwords.
Conclusion
In conclusion, while passwords have been the cornerstone of digital security for decades, their numerous shortcomings are increasingly apparent in our connected world.
As cyber threats evolve, so must our approach to securing our digital lives.
The future of digital security lies in innovative technologies like blockchain, which promise to offer a more secure, efficient, and user-centric approach to protecting our digital identities.
Blockchain: The Game-Changer in Digital Security
How Does Blockchain Enhance Security?
In the digital world, where data breaches and cyber threats loom large, blockchain emerges as a beacon of hope, promising a more secure and trustworthy online environment.
But what exactly makes blockchain a game-changer in digital security? Let’s unpack this.
The Immutable Ledger: A Foundation of Trust
At its core, blockchain is a distributed ledger technology. Imagine a ledger that is not maintained by a single entity but is spread across a network of computers, each holding a copy of the ledger.
This decentralization is key to blockchain’s power. Once a record is added to the blockchain, altering it is next to impossible.
This immutability provides a foundation of trust and security unprecedented in digital transactions.
Decentralization: The Antidote to Centralized Risk
Centralization in traditional digital systems creates a single point of failure, a treasure trove for cybercriminals. Blockchain disrupts this by distributing data across a vast network, thereby diluting the risk.
Even if a part of the network is compromised, the rest remains unscathed, preserving the integrity of the entire system.
Cryptography: The Art of Secret Keeping
Blockchain employs advanced cryptography to secure the data.
Each block in the chain is secured with a cryptographic hash, a mathematical algorithm that turns data into a unique string of characters. Any change in the data alters the hash dramatically.
This means that tampering with a block would require altering all subsequent blocks, an almost Herculean task given the computational power required.
Transparency and Anonymity: A Balancing Act
Blockchain strikes a unique balance between transparency and anonymity.
While all transactions are visible to everyone in the network, the identities of the parties involved are protected.
This transparency ensures accountability and trust, while anonymity safeguards user privacy.
Smart Contracts: The Protocols of Trust
Smart contracts, self-executing contracts with the terms of the agreement directly written into code, are a revolutionary aspect of blockchain.
They automate and enforce contractual obligations, reducing the need for intermediaries and the risk of fraud or manipulation.
Beyond Cryptocurrency: Diverse Applications of Blockchain in Security
Blockchain’s potential extends far beyond the realms of cryptocurrency.
In digital identity verification, it offers a secure way to manage and authenticate identities without centralized databases.
In supply chain management, it ensures the authenticity and traceability of products. In voting systems, it can provide secure and transparent electoral processes.
Challenges in Blockchain Adoption
Despite its potential, blockchain’s adoption faces hurdles.
Scalability, energy consumption, and the integration with existing systems are significant challenges. Furthermore, regulatory uncertainties and a lack of widespread understanding of the technology hinder its broader acceptance.
Preparing for a Blockchain-Enabled Future
As we stand on the brink of a blockchain revolution in digital security, it’s essential to educate ourselves about this technology.
Businesses and individuals alike must stay informed about the latest developments in blockchain and explore how it can be integrated into their digital practices.
Conclusion
Blockchain technology offers a new paradigm in digital security, promising a more secure, transparent, and efficient way to safeguard digital assets and identities.
As we move forward, embracing this technology and overcoming its challenges will be key to building a safer digital world.

The Mechanics of Blockchain Security
Understanding the Nuts and Bolts
Blockchain security is often hailed as a groundbreaking innovation, but how does it really work? What makes it so secure and reliable?
Let’s dive into the mechanics of blockchain security and understand what sets it apart.
The Anatomy of a Blockchain
Picture a blockchain as a series of digital ‘blocks’ linked together in a chain.
Each block contains a set of transactions or data, securely encrypted.
Every time a new block is added, it is verified by multiple nodes (computers) in the network, making fraud or alteration extremely difficult.
The Power of Decentralization
Decentralization is the heartbeat of blockchain security.
Unlike traditional systems where data is stored on central servers, blockchain distributes data across a network of nodes.
This means there’s no single point of failure, making it incredibly resistant to cyber-attacks and data breaches.
Cryptography: The Backbone of Blockchain Security
Blockchain uses advanced cryptographic techniques. Each block contains a unique cryptographic hash of the previous block, creating a secure link.
Altering any information would change the hash, alerting the network to the tampering. This cryptographic chaining ensures the integrity and chronological order of the blockchain.
Consensus Protocols: Ensuring Network Agreement
Blockchain operates on consensus protocols, rules that dictate how transactions are verified and added to the block.
Popular protocols like Proof of Work (PoW) and Proof of Stake (PoS) ensure that all nodes in the network agree on the state of the ledger, preventing fraudulent transactions.
Smart Contracts: Automating Trust
Smart contracts on the blockchain automatically execute transactions when predetermined conditions are met.
These contracts run on code and eliminate the need for intermediaries, reducing the risk of manipulation and increasing efficiency.
Challenges and Limitations
Despite its strengths, blockchain isn’t without challenges.
Issues like scalability, energy consumption (especially with PoW), and integrating blockchain into existing systems remain significant hurdles.
There’s also the concern of ‘51% attacks’ in some blockchains, where if more than half the network’s computing power is controlled by one entity, they could potentially manipulate the network.
Conclusion
Blockchain security offers a robust and innovative approach to protecting digital information.
Its combination of decentralization, cryptography, and consensus protocols provides a level of security far beyond traditional methods.
As the technology matures and overcomes its current limitations, blockchain stands to revolutionize how we secure our digital world.
Blockchain vs. Passwords: A Comparative Analysis
Why Blockchain Wins
In the digital security arena, blockchain and traditional passwords represent two very different philosophies.
While passwords have been the cornerstone of digital security for decades, blockchain introduces a paradigm shift.
Let’s compare these two to understand why blockchain is emerging as the superior option.
Traditional Passwords: The Aging Security Guard
Think of traditional passwords as an aging security guard. They’ve been around for a long time, are familiar, but they’re not as effective as they used to be.
Passwords are vulnerable to a range of attacks – from brute force to phishing – and they rely heavily on human memory and behavior, which can be fallible.
Blockchain: The Digital Fort Knox
On the other hand, blockchain can be likened to a digital Fort Knox. It doesn’t rely on single-key entry like passwords.
Instead, it offers a distributed, immutable ledger with complex cryptographic techniques.
This makes blockchain inherently more secure, as altering any part of the chain would require an astronomical amount of computing power.
User Experience: Complexity vs. Simplicity
One of the biggest drawbacks of passwords is their complexity and the user fatigue they cause. In contrast, blockchain can streamline the user experience.
With blockchain, users can potentially have a single digital identity for multiple platforms, eliminating the need to remember numerous passwords.
Decentralization: Eliminating Single Points of Failure
Passwords often involve centralized databases, creating single points of failure. Blockchain distributes data across a vast network, significantly reducing this risk.
Even if a part of the network is compromised, the rest remains secure, safeguarding the overall integrity.
Recovery and Revocation: A Clear Winner
Losing a password can lead to a cumbersome recovery process. Blockchain offers a more resilient approach.
For instance, with decentralized identity solutions, users can recover their identity through distributed mechanisms, without relying on a central authority.
Scalability and Adoption Challenges
Despite its advantages, blockchain faces its own set of challenges, particularly in scalability and widespread adoption.
Integrating blockchain into existing systems and ensuring it can handle large volumes of transactions are areas that need addressing.
Conclusion
Comparing blockchain with traditional passwords illustrates why blockchain is poised to be the future of digital security.
Its decentralized nature, enhanced security features, and user-friendly potential make it a formidable tool against cyber threats.
As blockchain technology overcomes its current challenges, it could render traditional passwords obsolete, ushering in a new era of digital security.
Real-World Applications of Blockchain in Security
Blockchain in Action
The realm of blockchain extends far beyond the confines of cryptocurrency.
Its unique attributes are being harnessed in various sectors, revolutionizing the way we think about and implement digital security.
Let’s explore some of the most impactful real-world applications of blockchain technology.
Revolutionizing Digital Identity Verification
One of the most significant applications of blockchain is in digital identity verification.
Traditional methods of identity verification are fraught with risks – from data breaches to identity theft.
Blockchain introduces a decentralized approach, where users can control their digital identities without relying on a central authority. This method not only enhances security but also offers greater privacy and control to individuals.
Transforming Supply Chain Management
In supply chain management, blockchain is a game-changer.
It provides a transparent and tamper-proof record of transactions and movements of goods.
This transparency ensures the authenticity of products, combats counterfeit goods, and enhances trust among consumers and businesses alike. From farm to table or manufacturer to retailer, every step is verifiable and secure.
Secure Voting Systems
Blockchain is making strides in securing electoral processes.
By leveraging blockchain, voting systems can become more secure, transparent, and resistant to tampering. This application could revolutionize democracy, making elections more accessible and trustworthy.
Healthcare Data Management
In healthcare, blockchain can securely manage patient records, ensuring privacy and data integrity.
It provides a secure platform for sharing medical records between authorized individuals and institutions, improving the efficiency and accuracy of diagnoses and treatments.
Challenges and Considerations
While these applications are promising, challenges such as scalability, regulatory compliance, and integration with existing systems remain.
There is also a need for a broader understanding and acceptance of blockchain technology among the general public and within specific industries.
Conclusion
The real-world applications of blockchain in security demonstrate its potential to revolutionize how we manage and protect digital information.
As the technology evolves and these challenges are addressed, blockchain is set to play a pivotal role in shaping a more secure and efficient digital world.
Overcoming the Challenges of Implementing Blockchain
Tackling the Obstacles
Blockchain technology, despite its potential, is not without its challenges.
Implementing blockchain in existing systems and processes requires navigating a complex landscape of technical, regulatory, and practical hurdles.
Let’s delve into these challenges and explore how they can be overcome.
Scalability: The Growing Pains of Blockchain
One of the primary challenges facing blockchain is scalability.
As the number of transactions on a blockchain increases, so does the need for greater computational power and storage.
This can lead to slower transaction times and higher costs, making it less practical for large-scale applications.
Solutions like sharding, where the blockchain is divided into smaller, more manageable pieces, and layer 2 solutions that process transactions off the main chain, are being explored to address this issue.
Energy Consumption: A Sustainable Dilemma
Blockchain, especially those using Proof of Work (PoW) consensus mechanisms, can be energy-intensive.
This raises concerns about the environmental impact of blockchain technologies.
Transitioning to more energy-efficient consensus mechanisms like Proof of Stake (PoS) or exploring renewable energy sources for mining operations are ways to mitigate this issue.
Regulatory Hurdles: Navigating the Legal Landscape
The decentralized and often borderless nature of blockchain poses significant regulatory challenges. Different countries have varying regulations regarding digital transactions, data privacy, and cryptocurrency.
Ensuring compliance while fostering innovation requires a delicate balance and ongoing dialogue between technology providers, users, and regulatory bodies.
Integration with Existing Systems
Integrating blockchain technology with existing digital infrastructures can be complex. Compatibility issues, the need for technical expertise, and the disruption of established processes can pose significant barriers.
Developing user-friendly blockchain solutions and providing education and training can facilitate smoother integration.
Security Concerns: Addressing Vulnerabilities
While blockchain is inherently secure, it is not immune to risks.
Potential security issues, such as 51% attacks, smart contract vulnerabilities, and key management challenges, need to be addressed.
Continuous research and development, alongside robust security protocols, are essential to bolster blockchain security.
Conclusion
Overcoming the challenges of implementing blockchain is crucial for realizing its full potential.
This involves addressing scalability and energy consumption issues, navigating regulatory landscapes, integrating with existing systems, and bolstering security measures.
As we tackle these obstacles, blockchain’s promise in transforming digital security becomes increasingly attainable.
The Future of Blockchain in Personal Security
What Lies Ahead
The horizon of personal security is being redrawn by blockchain technology.
As we edge further into the digital era, blockchain is poised to play a critical role in shaping our digital identities and safeguarding our online activities.
Let’s explore the promising future of blockchain in personal security.
Blockchain as a Guardian of Digital Identities
Imagine a world where your digital identity is as unique and unforgeable as your DNA.
Blockchain makes this possible. With its ability to create tamper-proof digital identities, blockchain is setting the stage for a future where identity theft and fraud become relics of the past.
These blockchain-based identities could replace traditional login credentials, offering a more secure and convenient way to access online services.
Enhanced Privacy and Control Over Personal Data
In an age where data breaches are commonplace, blockchain offers a beacon of hope. It empowers individuals with greater control over their personal data.
Instead of entrusting personal information to multiple organizations, blockchain allows individuals to store their data securely and share it selectively, using cryptographic keys.
Decentralized Finance (DeFi) and Personal Wealth Management
The rise of decentralized finance (DeFi) is another area where blockchain is set to transform personal security. By removing intermediaries, DeFi platforms offer more control and security over personal financial transactions.
Blockchain’s transparency and security features make it an ideal backbone for these platforms, promising a more secure and equitable financial ecosystem.
Challenges and Opportunities in Personal Security
The journey towards a blockchain-powered future is not without challenges.
Issues like public acceptance, technological literacy, and regulatory frameworks need to be addressed.
However, these challenges also present opportunities for innovation, collaboration, and education in the realm of personal security.
Conclusion
As blockchain technology matures, its potential to redefine personal security is immense.
From securing digital identities to revolutionizing personal finance, blockchain stands as a pillar of trust and security in the digital world.
Embracing this technology could lead us to a future where our digital lives are more secure, private, and under our control.
How to Prepare for the Blockchain Revolution
Getting Ready for Change
The blockchain revolution is not just coming; it’s already here. But how do we prepare for this seismic shift in digital security?
Whether you’re an individual, a business leader, or a technology enthusiast, gearing up for the blockchain era requires a proactive approach. Here’s how to get ready.
Educating Yourself and Your Team
Knowledge is power, especially when it comes to emerging technologies. Start by educating yourself about blockchain technology.
Online courses, webinars, and industry conferences are great resources. If you’re leading a team or an organization, consider facilitating blockchain training sessions to stay ahead of the curve.
Evaluating Blockchain Applications in Your Life or Business
Look at how blockchain could apply to your personal life or your business operations.
This might involve exploring blockchain-based solutions for data storage, identity verification, or even investment opportunities in the blockchain space.
Participating in Blockchain Communities and Networks
Engagement with blockchain communities can provide invaluable insights and keep you updated on the latest trends and developments.
Online forums, social media groups, and local meetups can serve as platforms for discussion and networking.
Experimenting with Blockchain Technologies
Hands-on experience is one of the best ways to understand blockchain.
Consider experimenting with blockchain applications, such as using a blockchain-based service or investing in cryptocurrencies.
This practical exposure can demystify the technology and reveal its potential applications in your life.
Understanding the Regulatory Landscape
Stay informed about the regulatory environment surrounding blockchain technology, especially if you’re considering it for business applications.
Keeping abreast of legal and compliance issues is crucial to navigating the blockchain space successfully.
Conclusion
Preparing for the blockchain revolution involves education, experimentation, and engagement with the blockchain community.
By taking these steps, individuals and businesses can position themselves to harness the benefits of blockchain technology and navigate the challenges it presents.
The future belongs to those who are ready to embrace change and innovate, and blockchain is a field ripe with opportunities for both.
Debunking Myths about Blockchain Security
Separating Fact from Fiction
Blockchain technology, while revolutionary, is often shrouded in myths and misconceptions, especially regarding its security aspects.
It’s crucial to separate fact from fiction to understand the true capabilities and limitations of blockchain security. Let’s debunk some common myths.
Myth 1: Blockchain is Inherently Invulnerable
Fact: While blockchain’s design makes it highly secure, it’s not infallible. Issues like code vulnerabilities in smart contracts and potential 51% attacks on certain types of blockchains can pose risks.
However, compared to traditional databases, blockchain’s decentralized and cryptographic nature makes it significantly more secure against common cyber threats.
Myth 2: All Blockchains are Public and Transparent
Fact: Not all blockchains are created equal.
While public blockchains offer transparency and decentralization, private blockchains control access more strictly, offering privacy and efficiency.
The choice between public and private blockchains depends on the specific needs and context of use.
Myth 3: Blockchain and Cryptocurrency are Interchangeable
Fact: Cryptocurrencies like Bitcoin are just one application of blockchain technology.
Blockchain has a myriad of other applications beyond digital currencies, from supply chain management to digital identity verification.
Myth 4: Blockchain Transactions are Always Anonymous
Fact: Anonymity in blockchain transactions varies. While cryptocurrencies like Bitcoin offer a degree of anonymity, other blockchains provide full transparency.
Moreover, advanced techniques can sometimes trace blockchain transactions, challenging the notion of absolute anonymity.
Myth 5: Blockchain is a Data Privacy Solution
Fact: Blockchain can enhance data security, but it doesn’t automatically guarantee data privacy.
The way data is recorded and encrypted on the blockchain plays a crucial role in determining privacy levels.
Conclusion
Understanding the realities of blockchain security is vital for its effective implementation and trust.
By debunking these myths, we can appreciate the true potential and limitations of blockchain, paving the way for informed and effective use of this transformative technology.
The Ultimate Guide to Blockchain Security Tools
Your Toolkit for the Future
As blockchain technology becomes increasingly prevalent, the importance of understanding and utilizing blockchain security tools grows.
Whether you’re a blockchain enthusiast, a business professional, or someone curious about the technology, having a grasp of these tools is essential.
Here’s a guide to some key blockchain security tools.
Cryptographic Wallets: Secure Storage for Digital Assets
Cryptographic wallets are essential for securely storing and managing digital assets like cryptocurrencies.
They use private keys, a form of cryptography, to enable users to access and transact their assets securely.
Choosing a reputable wallet, whether it’s a software, hardware, or paper wallet, is crucial for asset security.
Smart Contract Auditing Tools
As smart contracts become more complex, the need for thorough auditing increases.
Tools like Mythril and OpenZeppelin provide security analysis of smart contracts, identifying vulnerabilities and ensuring that they behave as intended.
Blockchain Explorers: Tracking Transactions
Blockchain explorers are tools that allow users to view and track transactions on a blockchain.
They offer transparency and the ability to verify transactions, which is crucial for trust and security in blockchain ecosystems.
Decentralized Identity Applications
Decentralized identity applications use blockchain to provide users with more control over their personal information.
These tools are foundational for creating secure digital identities and can be used for authentication purposes without the need for centralized databases.
API Security Tools
APIs are vital for blockchain applications, and securing them is paramount.
Tools like OAuth 2.0, OpenID Connect, and API gateways help secure and manage access to blockchain-based APIs, protecting against unauthorized access and data breaches.
Conclusion
The landscape of blockchain security tools is vast and evolving. Familiarizing oneself with these tools is a step towards harnessing the full potential of blockchain technology.
As blockchain continues to grow and integrate into various sectors, these tools will become instrumental in securing and optimizing blockchain applications.
Final Conclusion
As we journey through the intricate world of blockchain technology and its impact on digital security, it becomes evident that we are standing on the brink of a major technological revolution.
From debunking myths about blockchain security to exploring an array of advanced security tools, our expedition reveals a future where blockchain is poised to redefine the norms of digital safety and privacy.
This transformative technology, with its decentralized nature, cryptographic security, and innovative applications, offers more than just a new way to secure digital transactions; it promises a future where our digital identities and assets are protected with unprecedented robustness.
Embracing blockchain, understanding its potential, and preparing for its widespread adoption are crucial steps towards a safer, more secure digital world.
As we continue to explore and innovate in this exciting field, the possibilities for enhanced digital security seem limitless.
FAQs
Is blockchain technology applicable in everyday life, or is it just for tech experts?
Blockchain technology is increasingly becoming applicable in everyday life, not just for tech experts. Its applications range from secure online transactions and digital identity management to supply chain tracking and voting systems, making it relevant and beneficial for the general public.
Can blockchain be used to secure all kinds of digital data, or is it limited to financial transactions?
Blockchain can secure various kinds of digital data, not just financial transactions. Its applications include securing personal data, healthcare records, digital identities, and more, demonstrating its versatility beyond just financial uses.
How does blockchain technology offer more security compared to traditional security methods?
Blockchain technology offers more security through its decentralized structure, which eliminates single points of failure, and its use of advanced cryptography, which ensures data integrity and prevents unauthorized alterations.
Are there any significant environmental concerns associated with blockchain technology?
Yes, certain blockchain implementations, particularly those using Proof of Work (PoW) consensus mechanisms, can be energy-intensive and raise environmental concerns. However, newer technologies like Proof of Stake (PoS) are more energy-efficient and are being adopted to address these concerns.
How can individuals ensure they are using blockchain technology safely and effectively?
Individuals can ensure safe and effective use of blockchain technology by educating themselves about its basics, using reputable blockchain services and wallets, staying informed about security best practices, and being cautious of scams and fraudulent schemes in the blockchain space.
Verified Source References
- Blockchain Technology Fundamentals: IBM Blockchain Essentials
- Understanding Cryptographic Wallets: Investopedia – Cryptocurrency Wallets
- Guide to Smart Contract Auditing Tools: Ethereum Smart Contract Best Practices
- Blockchain Explorers and Their Use: Blockgeeks – Blockchain Explorers
- Decentralized Identity Applications in Blockchain: Decentralized Identity Foundation
Artifiсiаl Intelligenсe
Web3 Revolution: Decentralize Everything and Rewrite the Rules

Web3 Revolution: Decentralize Everything and Rewrite the Rules
In an era where digital innovation is not just a trend but a necessity, the emergence of Web3 is revolutionizing how we perceive and interact with the internet.
The journey from Web1, a read-only web, to Web2, characterized by interactivity and social media, has been transformative.
Now, Web3 is poised to take a giant leap forward, advocating for a decentralized, blockchain-based internet, promising to enhance user autonomy and disrupt traditional power structures.
But why is decentralization so crucial, and how will it impact society at large?
Web3 is not just a technological upgrade; it’s a paradigm shift. It’s about redistributing power from centralized authorities to the edges of the network, to the users themselves.
This shift has profound implications for everything from finance to personal identity, challenging the status quo and offering a more inclusive and equitable digital future.
As we delve deeper into the world of Web3, we uncover key concepts like Decentralized Finance (DeFi), Non-fungible Tokens (NFTs), and decentralized social media platforms that are not just buzzwords but harbingers of a new digital era.
These innovations are rewriting the rules of engagement, ownership, and participation in the digital realm.
However, the path to a fully decentralized world is not without its challenges. Issues like scalability, security, and regulatory compliance pose significant hurdles.
Moreover, the environmental impact of blockchain technologies and the digital divide are concerns that need urgent addressing.
As we embark on this journey through the article, we will explore the multifaceted aspects of Web3 and decentralization, analyzing their potential, challenges, and the future they promise.
Join us in uncovering the depths of this digital revolution and envision a future where the internet is not just a tool, but an extension of our collective will, decentralized and democratic.
Understanding Web3 and Decentralization
The journey from Web1 to Web3 marks a significant evolution in the internet’s history.
Initially, Web1 offered a static experience, where users were mere consumers of content. The transition to Web2 brought interactivity, with platforms like social media allowing users to be both creators and consumers.
However, this era also centralized power in the hands of a few large tech companies, raising concerns about privacy, data ownership, and control.
Enter Web3, the next internet frontier, built on the principles of decentralization and blockchain technology.
It promises to return control and ownership back to the users. In this new paradigm, data is distributed across a blockchain network, ensuring transparency, security, and resistance to censorship.
Key technologies driving Web3 include blockchain, which provides a decentralized ledger for transparent and tamper-proof record-keeping; smart contracts, which are self-executing contracts with the terms directly written into code; cryptocurrencies, digital or virtual currencies secured by cryptography, and decentralized applications (dApps), which run on a blockchain network instead of being hosted on centralized servers.
Decentralization is not just a technological advancement; it’s a societal shift.
By democratizing access and control over the internet, Web3 has the potential to reduce the power imbalances seen in today’s digital landscape.
It opens up new opportunities for individual empowerment, privacy protection, and equitable participation in the digital economy. However, realizing this potential requires overcoming technical, regulatory, and societal challenges inherent in such a transformative shift.
Evolution from Web1 to Web3
The internet’s evolution is a story of constant change and innovation.
In its earliest form, Web1, the internet was a collection of static webpages, akin to a digital encyclopedia. This era was defined by limited user interaction and content creation, dominated by read-only websites.
Then came Web2, an interactive and social web, where users became creators. Platforms like Facebook, YouTube, and Twitter facilitated unprecedented levels of participation, collaboration, and information sharing.
However, this era also saw the rise of centralization, with a few large companies controlling vast swathes of the online landscape.
Enter Web3, a paradigm shift towards a decentralized internet. This new era is built on the backbone of blockchain technology, offering a decentralized, transparent, and user-centric experience.
Web3 represents a significant departure from the monopolized structure of Web2, emphasizing user sovereignty and data privacy. It’s an internet where users are not just consumers but also owners and stakeholders in the platforms they use.
Significance of Decentralization in Society
Decentralization is more than a technological concept; it’s a movement towards redistributing power and control.
In a decentralized system, there is no central point of control or failure. This architecture has profound implications for society, especially in terms of data ownership, privacy, and security.
Decentralization challenges the status quo of how data is managed, stored, and utilized, offering a more democratic model where users have greater control over their information.
This shift has the potential to remodel various societal structures, from finance to governance. Decentralization promises to reduce the influence of intermediaries, lower barriers to entry, and foster a more equitable distribution of resources and opportunities.
It’s about creating a more balanced digital ecosystem where the benefits of technology are accessible to all, not just a select few.
Key Concepts and Technologies in Web3
Web3 is underpinned by several key concepts and technologies:
- Blockchain: At the heart of Web3 is blockchain technology, a distributed ledger that records transactions across many computers, ensuring transparency, security, and immutability.
- Smart Contracts: These are self-executing contracts with the terms of the agreement directly written into code, enabling trustless and automated transactions.
- Cryptocurrencies and Tokens: Digital currencies and assets play a crucial role in Web3, facilitating transactions and incentivizing network participation.
- Decentralized Applications (dApps): These applications run on a decentralized network, rather than a single computer, enhancing security and resistance to censorship.
These technologies together form the backbone of the Web3 ecosystem, providing a foundation for a new internet era where trust, transparency, and user empowerment are paramount.
The Most Radical Decentralized Projects Changing the World
Decentralized projects in the Web3 space are not just technological innovations; they are redefining entire industries and societal structures.
Decentralized Finance (DeFi)
DeFi is reimagining the financial system by leveraging blockchain technology to create a more open, accessible, and transparent financial ecosystem.
Unlike traditional finance, DeFi operates without central financial intermediaries such as banks, exchanges, or insurance companies. It utilizes smart contracts on blockchains, predominantly Ethereum, to execute financial transactions, offering services like lending, borrowing, and trading in a trustless environment.
This innovation enables anyone with an internet connection to access financial services, bypassing geographical and socio-economic barriers.
DeFi’s potential to democratize finance is immense. It offers an alternative to those underserved by the traditional banking system, opening up possibilities for financial inclusion on a global scale.
However, the nascent nature of DeFi also brings challenges like high volatility, regulatory uncertainty, and security risks.
Non-fungible Tokens (NFTs)
NFTs have captured the world’s attention as a revolutionary way to represent ownership and authenticity of unique digital items using blockchain technology.
Unlike cryptocurrencies, NFTs are not interchangeable; each token is unique and holds distinct value. Initially popular in the art world, they allow artists to monetize digital works in ways previously impossible, offering proof of ownership and provenance.
The implications of NFTs extend beyond art into areas like real estate, gaming, and digital identity.
They represent a significant shift in how we understand ownership and value in the digital realm, challenging traditional models of intellectual property and asset management.
Decentralized Identity Solutions
Decentralized identity solutions seek to return control of personal data to individuals. Leveraging blockchain technology, these solutions enable users to create and manage their digital identities without relying on centralized authorities.
This approach enhances privacy, reduces the risk of data breaches, and gives users control over how their personal information is shared and used.
In a world increasingly concerned with data privacy and security, decentralized identity solutions offer an alternative to the centralized models of digital identity management, often prone to misuse and exploitation.
Decentralized Social Media and Content Platforms
Decentralized social media and content platforms aim to address the challenges of censorship, privacy, and data control prevalent in traditional, centralized platforms.
By leveraging blockchain technology, these platforms allow users to control their data, monetize their content, and engage in a more transparent and equitable online environment.
These platforms challenge the existing social media paradigm, offering a vision of the internet where freedom of expression and user empowerment are central.
Decentralized Computing and Storage Solutions
Decentralized computing and storage solutions, such as IPFS and Filecoin, offer an alternative to centralized cloud storage and computing services.
These decentralized networks allow users to store and access data across a distributed network of nodes, enhancing security, privacy, and resistance to censorship.
By decentralizing data storage and computation, these solutions not only offer a more robust and secure infrastructure but also challenge the monopolistic hold of big tech companies over data storage and computing resources.
The Challenges and Risks of Decentralization
While the promise of Web3 and decentralization is immense, it’s not without its challenges and risks.
Scalability and Performance Issues
One of the most significant challenges facing decentralized technologies is scalability. Blockchain networks, in particular, struggle to handle large volumes of transactions quickly and efficiently.
This limitation impacts the user experience and hinders the widespread adoption of decentralized applications.
Solutions like layer-2 scaling (e.g., Lightning Network for Bitcoin, Plasma and Rollups for Ethereum) and alternative consensus mechanisms (e.g., Proof of Stake) are being developed.
However, achieving scalability without compromising security and decentralization remains a complex challenge.
Security Concerns and Potential Attacks
The decentralized nature of blockchain and related technologies brings unique security challenges.
Smart contracts, despite their potential, are susceptible to bugs and vulnerabilities, which can lead to significant losses. The decentralized autonomous organizations (DAOs) are not immune to attacks, as seen in various high-profile cases.
Ensuring the security of decentralized networks and applications requires constant vigilance, innovative security solutions, and a community-driven approach to identify and address vulnerabilities.
Regulatory Hurdles and Legal Considerations
The decentralized world exists in a regulatory grey area. Many countries are still grappling with how to regulate cryptocurrencies, DeFi, NFTs, and other decentralized technologies.
The lack of clear regulations creates uncertainty for investors, developers, and users.
Regulators face the challenge of protecting consumers and preventing illicit activities while not stifling innovation in this rapidly evolving space.
Finding a balance between regulation and innovation is key to the sustainable growth of decentralized technologies.
Environmental Impact and Sustainability
The environmental impact of certain blockchain technologies, especially those relying on energy-intensive Proof of Work (PoW) consensus mechanisms, is a growing concern.
The high energy consumption associated with mining activities, primarily for cryptocurrencies like Bitcoin, has led to debates about the sustainability of these technologies.
In response, there is a growing shift towards more energy-efficient consensus mechanisms like Proof of Stake (PoS).
The industry is also exploring renewable energy sources and more sustainable practices to mitigate the environmental impact.
The Digital Divide and Equitable Access
While decentralized technologies offer numerous benefits, there’s a risk that they could exacerbate the digital divide.
Access to these technologies requires not only internet connectivity but also a certain level of technical expertise and financial resources.
Ensuring equitable access to the benefits of decentralization is essential. This includes making these technologies more user-friendly, affordable, and accessible to people across different socio-economic backgrounds.
The Future of Web3 and Decentralization
The future of Web3 and decentralization holds immense possibilities, but it also presents new challenges and questions.
Emerging Trends and Innovations
The field of Web3 and decentralization is rapidly evolving, with new trends and innovations emerging regularly.
Interoperability between different blockchain networks is a key focus, allowing for seamless interaction between various decentralized applications and services.
Advancements in blockchain scalability, such as sharding and new consensus algorithms, are also critical for the future growth of decentralized networks.
These innovations will enable more efficient, scalable, and sustainable decentralized systems.
The Role of AI in Shaping the Decentralized World
AI has the potential to significantly impact the decentralized world. AI-driven analytics can enhance the functionality of decentralized applications, providing insights and optimizing network operations.
Smart contracts, powered by AI, could automate complex processes and decision-making, further enhancing the efficiency and capabilities of decentralized systems.
The integration of AI and blockchain could lead to more intelligent, autonomous, and efficient decentralized networks. However, this convergence also raises new ethical and security considerations that need to be addressed.
Societal Implications and Ethical Considerations
The shift towards a more decentralized internet raises important societal and ethical questions.
Issues like data privacy, equitable access, and the redistribution of economic and social power are at the forefront.
As decentralized technologies become more prevalent, it’s essential to consider their impact on society.
This includes ensuring that the benefits of these technologies are accessible to all and that they are used in a way that promotes fairness, equity, and social good.
Vision for a More Inclusive and Decentralized Future
The ultimate vision of Web3 and decentralization is a more inclusive, equitable, and user-empowered internet.
This vision encompasses greater financial inclusion through DeFi, enhanced personal privacy and control through decentralized identity solutions, and new opportunities for creators and innovators.
Achieving this vision will require not only technological advancements but also a concerted effort to address the societal and ethical implications of these technologies.
It’s about building a digital ecosystem that is open, transparent, and accessible to all.
Conclusion
As we delve into the intricacies of Web3 and its decentralized ethos, it’s clear that we are standing at the cusp of a digital revolution.
This new internet age, characterized by blockchain, smart contracts, and decentralized applications, is not just a technological leap but a societal one.
It offers a glimpse into a future where power is not hoarded by a few but distributed among many, where privacy is a right, not a privilege, and where digital identity is controlled by the individual, not corporations.
The road ahead for Web3 and decentralization is fraught with challenges.
Technical hurdles like scalability and security, legal and regulatory ambiguities, and concerns about environmental sustainability and the digital divide must be navigated carefully.
However, the potential benefits— a more inclusive, equitable, and user-empowered digital world — are immense.
The Web3 revolution is not just about technology; it’s about reimagining and reshaping the very fabric of the internet and, by extension, society. It’s about building a digital ecosystem that is open, transparent, and accessible to all, regardless of geography or background.
As we move forward, it will be crucial for developers, users, regulators, and all stakeholders to work collaboratively to overcome the challenges and realize the full potential of this new decentralized world.
In this journey, every individual has a role to play, whether as a developer, a content creator, an investor, or simply as an informed and engaged user.
The future of the internet is not just being written; it’s being decentralized. And in this decentralization lies the promise of a more democratic, equitable, and innovative digital future.
FAQs
What is Web3?
Web3, often termed as the third generation of the internet, represents a new paradigm in how we interact with the web. Unlike its predecessors, Web3 is built on the foundation of decentralization and blockchain technology.
In simple terms, it’s an iteration of the web where data and content are not controlled by centralized entities like corporations or governments, but are instead distributed across a network of users. This decentralization offers a more secure, transparent, and user-centric internet experience.
At the heart of Web3 is the idea that users, not just a few big players, have ownership and stake in the online platforms and communities they participate in.
This is facilitated through technologies like blockchain, smart contracts, and cryptocurrencies, which enable a level of security and trust not seen in previous web iterations.
Essentially, Web3 gives power back to the users, allowing them to control their data, transact securely without intermediaries, and interact in a truly global digital ecosystem.
How does Decentralization Impact Society?
Decentralization, the core principle of Web3, has profound societal implications.
It redistributes power from centralized authorities to individuals, potentially leading to a more democratic and equitable digital landscape. In a decentralized system, individuals have more control over their data, their online interactions, and, importantly, their digital identities.
This shift can reduce the influence of large corporations and governments in the digital realm, fostering a more balanced and fair internet.
Moreover, decentralization can enhance privacy and security, as data isn’t stored in a single location that could be a target for hackers.
It also opens the door for greater financial inclusion through decentralized finance (DeFi) systems, where traditional banking and financial barriers are removed, allowing more people to access financial services.
In a broader sense, decentralization can lead to more innovative and diverse online ecosystems, as it encourages community-led governance and development.
What are the Major Challenges Facing Web3?
Web3, despite its potential, faces significant challenges. Scalability is one of the foremost issues.
As decentralized networks grow in size, they often struggle to process transactions quickly and efficiently, which can lead to congestion and high transaction fees. This scalability challenge is a barrier to widespread adoption, as it impacts the user experience.
Security is another major concern. While blockchain, the underlying technology of Web3, is generally secure, the applications built on top of it, like smart contracts and decentralized apps (dApps), can have vulnerabilities.
These vulnerabilities can lead to hacks and other security breaches, posing risks to users and the integrity of the decentralized networks.
Finally, user experience (UX) and adoption are challenges.
Web3 technologies often have a steep learning curve, and the lack of user-friendly interfaces can deter mainstream users from adopting these new technologies.
Can Web3 Coexist with Current Regulatory Frameworks?
The coexistence of Web3 with current regulatory frameworks is a complex issue. On one hand, the decentralized and often borderless nature of Web3 presents challenges to traditional regulatory models, which are typically nation-centric.
Regulations around data privacy, financial transactions, and digital assets are areas where existing laws may struggle to accommodate the nuances of decentralized technologies.
On the other hand, there’s a growing recognition of the need for regulation to evolve in response to these new technologies.
This evolution could mean developing new frameworks that address the unique aspects of decentralization while ensuring user protection, security, and stability.
The key will be finding a balance where regulation supports innovation in the Web3 space without stifling it.
What Role Will AI Play in the Future of Web3?
AI is poised to play a significant and transformative role in the future of Web3. The intersection of AI and Web3 can lead to more intelligent, efficient, and personalized online experiences.
AI algorithms can be used to analyze blockchain data, providing insights that can improve the efficiency and security of decentralized networks.
In decentralized finance, AI can aid in risk assessment, fraud detection, and automated trading. In content and social media platforms, AI can help in curating personalized content, managing community governance, and moderating content in a decentralized context.
Moreover, the integration of AI with decentralized technologies could lead to the development of more autonomous and intelligent dApps, enhancing user interaction and functionality.
However, this integration also raises important questions about privacy, security, and the ethical use of AI in a decentralized environment.
cryptocurrencies
Busting Myths: Can You REALLY Make Money in Axie Infinity’s Metaverse?

Busting Myths: Can You REALLY Make Money in Axie Infinity‘s Metaverse?
Ah, Axie Infinity. The once-obscure blockchain game that transformed into a pop culture phenomenon, spawning Axie millionaires and igniting a frenzy for all things “play-to-earn.”
But with the hype comes the inevitable skepticism. Can you really make money in Axie Infinity’s metaverse, or is it just a digital mirage shimmering in the crypto-desert?
Strap in, fellow adventurers, because we’re about to bust some Axie-sized myths and uncover the gritty reality of earning in this virtual wonderland.
Myth #1: Axie Infinity is a cash-grab pyramid scheme.
Ah, the dreaded “pyramid scheme” accusation.
Let’s address this head-on. Yes, Axie Infinity has elements of a network marketing system, where early players benefit from onboarding new Axie trainers.
But unlike a true pyramid scheme, Axie’s value isn’t solely dependent on constant recruitment.
Think of Axies as Pokemon crossed with digital real estate. Each Axie is a unique NFT (non-fungible token) with distinct genes and battle capabilities.
Their value fluctuates based on demand, breeding potential, and in-game performance. So, even if player recruitment slows down, Axies themselves can retain value due to their inherent utility and collectability.
Myth #2: You need a small fortune to get started.
While it’s true that the initial cost of purchasing an Axie has skyrocketed (some costing thousands of dollars!), Axie Infinity’s scholarship program offers a glimmer of hope.
Scholarships pair experienced players with “scholars” who borrow Axies to play and compete, sharing a percentage of their earnings.
It’s not a get-rich-quick scheme, but it’s a fantastic way to test the waters without breaking the bank.
Myth #3: All you do is grind battles and earn easy crypto.
Okay, let’s dispel this fantasy right now.
Axie Infinity isn’t some passive income machine where you click buttons and watch the crypto roll in. It’s a strategy game with a steep learning curve.
Mastering Axie breeding, team composition, and battle tactics takes time, dedication, and a healthy dose of skill. Think of it like any other competitive career – success requires hard work, strategic thinking, and a bit of luck.
But wait, there’s more!
We’ve only scratched the surface of Axie Infinity’s earning potential. Buckle up for deeper dives into:
- Land Ownership: Own a piece of Lunacia, Axie’s virtual land, and reap the rewards of resource harvesting, Axie breeding bonuses, and community events.
- Breeding and Marketplace Mastery: Craft coveted Axies with high battle potential, then flip them for handsome profits on the Axie marketplace.
- Content Creation and Community Building: Share your Axie expertise through streams, tutorials, and guides, attracting sponsorships and loyal followers.
Is Axie Infinity a guaranteed path to riches? Not necessarily. But for those willing to invest time, skill, and strategic thinking, it offers genuine earning potential within a vibrant and ever-evolving metaverse.
Remember, it’s not just about “playing to earn”; it’s about building a sustainable future within a thriving play-to-own ecosystem.
Ready to embark on your Axie adventure? Dive into the following sections for detailed strategies, helpful resources, and cautionary tales from experienced players.
Let’s build something truly epic together, brick by digital brick, in the heart of Axie Infinity’s metaverse!
Axie Academy: Leveling Up Your Play-to-Earn Prowess
Now that we’ve debunked the myths and ignited your inner Axie adventurer, let’s get down to the nitty-gritty: how to actually earn in this blockchain playground.
Think of this as your Axie Academy crash course, equipping you with the knowledge and strategies to turn virtual battles into real-world rewards.
Mastering the Battle Arena:
- Team Synergy: Don’t just assemble a motley crew – build a cohesive team around complementary Axie classes and abilities. Research, experiment, and discover combos that dominate the battlefield.
- Daily Grind, Smart Grind: Yes, there’s an element of daily tasks and repetitive battles. But optimize your routine! Focus on high-reward activities, utilize energy efficiently, and avoid mindlessly grinding away your enthusiasm.
- Practice Makes Perfect: Hone your battle skills against other players, analyze mistakes, and learn from seasoned trainers. Remember, victory favors the prepared, not just the lucky.
Breeding for Profit:
- Understanding Axie Genes: It’s not just about aesthetics! Delve into gene combinations, traits, and recessive genes to breed Axies with high market value and battle prowess.
- Scholarship Star Power: Don’t underestimate the scholarship market. Breed Axies specifically tailored for scholar play, then offer them to aspiring trainers in exchange for a cut of their earnings.
- Trendspotting and Market Savvy: Stay ahead of the curve! Analyze Axie trends, identify in-demand traits, and breed Axies that fill the market gap – then watch your profits soar.

Beyond the Battlefield: Alternative Earning Avenues
- Land Ownership: From Baron to Tycoon: Invest in a slice of Lunacia, Axie’s virtual land. Build structures, harvest resources, host events, and rent out your land to fellow players for a steady stream of in-game currency.
- Content Creation: Axie Evangelist Extraordinaire: Share your Axie expertise through guides, streams, tutorials, and even artistic creations. Build a loyal community, attract sponsorships, and cash in on your content mastery.
- Community Building: Guild Mastermind: Forge alliances, create guilds, and organize tournaments. Facilitate collaboration, offer training to newcomers, and leverage your guild’s reputation to unlock lucrative partnerships and community-driven rewards.
Remember, this is just a roadmap, not a rigid itinerary. Experiment, discover your niche, and find what fuels your earning engine within the Axie ecosystem.
Navigating the Terrain: Tips and Resources for Aspiring Axie Earners
Scholarship Essentials:
- Finding the Right Axies: Choose Axies with balanced stats, easy-to-learn playstyles, and breeding potential to attract scholars.
- Crafting a Fair Contract: Clearly outline expectations, reward percentages, and dispute resolution mechanisms to ensure a smooth and mutually beneficial partnership.
- Community Matters: Join Axie scholarship communities, network with experienced trainers, and seek advice on building a successful program.
Avoiding Common Pitfalls:
- Don’t Chase Hype: Resist the temptation to buy into overhyped trends or Axies promising overnight riches. Stick to research, market analysis, and long-term strategies.
- Beware of Scams: The blockchain world is rife with scams. Stay vigilant, double-check contract terms, and never invest more than you can afford to lose.
- Remember, It’s a Game: Don’t get so caught up in earning that you forget to have fun! Axie Infinity is a vibrant community, filled with exciting gameplay, creative adventures, and genuine connections.
Beyond the Pixelated Curtain: Real-World Considerations
Tax Implications:
Understand the tax regulations surrounding cryptocurrency earnings in your region. Consulting a financial advisor is always recommended.
Time Investment vs. Reward:
Earning in Axie Infinity requires dedication and consistent effort. Be realistic about the time commitment and weigh it against your expected returns.
Sustainable Play-to-Earn:
Treat Axie Infinity as a long-term endeavor, not a quick buck scheme. Build sustainable earning strategies, diversify your income streams, and adapt to the ever-evolving metaverse.
Remember, your Axie journey is just beginning. We’ve equipped you with the tools and knowledge, but the path forward is yours to forge. Embrace the challenges, celebrate the victories, and above all, have fun exploring the boundless possibilities of Axie Infinity’s metaverse.
Q1: Is Axie Infinity too late to invest in?
That’s a crucial question, and the answer depends on your investment goals and risk tolerance.
Axie Infinity has indeed seen tremendous growth, and some highly valued Axies have reached astronomical prices. However, entry costs at that level might not be sustainable for everyone.
Here’s the nuance:
- Early adopter advantage: While some of the initial explosive growth might be behind us, there’s still potential for value appreciation and earning opportunities within the Axie ecosystem. Land ownership, scholarships, and community-driven initiatives present new avenues for involvement.
- Evolving landscape: The play-to-earn landscape is constantly shifting, with new games and platforms emerging. Diversifying your portfolio across play-to-earn options alongside Axie Infinity can mitigate risk and potentially unlock broader earning potential.
- Time investment vs. reward: Remember, Axie Infinity isn’t a passive income machine. Be realistic about the time commitment required to learn, strategize, and actively participate in the economy to see substantial returns.
Ultimately, the decision is yours. Consider your financial situation, risk tolerance, and desired level of involvement before making any investment decisions.
Remember, thorough research and a long-term perspective are key to navigating the ever-evolving world of play-to-earn.
Q2: Can I really earn a living playing Axie Infinity?
It’s possible, but not guaranteed. Several factors influence your earning potential, including:
- Skill level: Mastering team synergies, breeding strategies, and efficient gameplay tactics significantly increases your earnings potential.
- Time commitment: The more hours you dedicate to daily tasks, battles, and market analysis, the higher your potential yield.
- Chosen earning avenue: Axies with high battle prowess will generate more income through Arena rewards, while scholarships and market-savvy breeding can also be lucrative.
- Market fluctuations: Cryptocurrency prices are volatile, so your earnings may fluctuate alongside the overall market trends.
Remember, Axie Infinity is a competitive environment. Treat it like any other career path – dedication, skill development, and strategic thinking are crucial for success.
Don’t solely rely on Axie Infinity for your livelihood, but consider it as one income stream within a diversified portfolio.
Q3: Are there risks involved in playing Axie Infinity?
Absolutely. Here are some key risks to consider:
- Investment risk: The value of Axies and cryptocurrency can fluctuate significantly, leading to potential financial losses.
- Scams and phishing: The blockchain world is prone to scams. Always exercise caution, double-check transactions, and never share sensitive information.
- Technical glitches and platform vulnerabilities: Blockchain platforms are still evolving, and technical issues can temporarily disrupt gameplay or impact your assets.
- Tax implications: Depending on your location, cryptocurrency earnings may be subject to taxes. Consult a financial advisor for guidance.
Mitigate these risks through prudent financial planning, thorough research, and responsible participation within the Axie community.
Q4: What resources can I use to learn more about Axie Infinity?
Several excellent resources are available to help you navigate the Axie Infinity ecosystem:
- The official Axie Infinity website: This site provides comprehensive information on gameplay, economics, and official updates.
- The Axie Infinity community forums: Connect with experienced players, ask questions, and learn from their expertise.
- Educational YouTube channels and online guides: Numerous channels and websites offer in-depth tutorials, strategies, and market analyses.
- Social media communities: Follow Axie Infinity and dedicated player communities on Twitter, Discord, and Telegram for the latest news and discussions.
Stay informed, stay engaged, and don’t hesitate to seek help from the supportive Axie community.
Q5: What’s the future of Axie Infinity and play-to-earn?
The future is brimming with possibilities! Here are some exciting trends to watch:
- Expanding metaverse ecosystems: Axie Infinity is likely to integrate with other blockchain games and platforms, creating a more interconnected and diverse metaverse experience.
- New earning models: Play-to-earn is evolving beyond just games. Look for innovative applications in sectors like music, art, and social experiences.
- Focus on sustainability: As play-to-earn matures, expect increased emphasis on long-term economic models, resource management, and community-driven governance.
The play-to-earn landscape is still in its early stages, brimming with innovation and potential. Embrace the possibilities, contribute to the community, and be a part of shaping the future of this exciting new frontier.
This concludes our comprehensive guide to navigating the Axie Infinity metaverse and unlocking its earning potential. Remember, the journey is as important as the destination. Enjoy the adventure, fellow Axie adventurer!
P.S.: Your Personal Axie Odyssey
Beyond the strategies and resources, remember, this Axie adventure is ultimately yours to own.
It’s not just about maximizing earnings; it’s about exploring, connecting, and forging your unique path within this vibrant digital world.
Here are some ways to personalize your Axie experience:
- Discover your passion: Go beyond the meta trends and find what sets your Axie spirit ablaze. Maybe it’s crafting the ultimate battle team, breeding prized Axies with distinct aesthetics, or building a thriving community within Lunacia.
- Embrace the creative canvas: Axie Infinity isn’t just about battling; it’s a platform for creative expression. Design elaborate Axie homes, host in-game events, or even craft Axie-inspired art and share it with the community.
- Forge meaningful connections: The Axie community is more than just fellow players; it’s a network of passionate individuals eager to collaborate, share knowledge, and build lasting friendships. Participate in community events, join guilds, and mentor newcomers – you’ll be surprised by the rewarding relationships you form.
- Contribute to the ecosystem: Don’t just be a passive participant; become an active contributor to the Axie world. Share your strategies, offer constructive feedback, and participate in governance proposals to shape the future of the metaverse.
Remember, your Axie journey is as unique as the Axie you breed. Embrace the possibilities, explore with an open mind, and leave your mark on this ever-evolving digital frontier.
Let your Axie spirit guide you, and who knows, perhaps you’ll become the next legendary Axie trainer, inspiring others with your own path to success and fulfillment within the metaverse.
With that, we bid you farewell, fellow adventurer. May your Axie journey be filled with thrilling battles, rewarding earnings, and lasting memories in the heart of the Axie Infinity metaverse!
Verified Source References:
- Axie Infinity Whitepaper: https://whitepaper.axieinfinity.com/
- Axie Infinity Blog: https://axieinfinity.com/
- Play to Earn Alliance: https://www.playtoearn.online/
- Cointelegraph: https://cointelegraph.com/tags/axie-infinity
- Forbes: https://www.forbes.com/sites/youngjoseph/2021/10/06/metaverse-heats-up-how-axie-infinitys-30b-valuation-led-crypto-game-frenzy/
-

 Education2 years ago
Education2 years agoCreating Engaging And Relevant Content As A Literacy Influencer
-

 Internet3 years ago
Internet3 years agoWhat Are the Differences Between WP Rocket, RocketCDN and Cloudflare
-

 How To..3 years ago
How To..3 years agoWhat Is Better Than Safety Deposit Box
-

 Mobile Phones3 years ago
Mobile Phones3 years agoKnow About the New Upcoming Mobile Phones
-
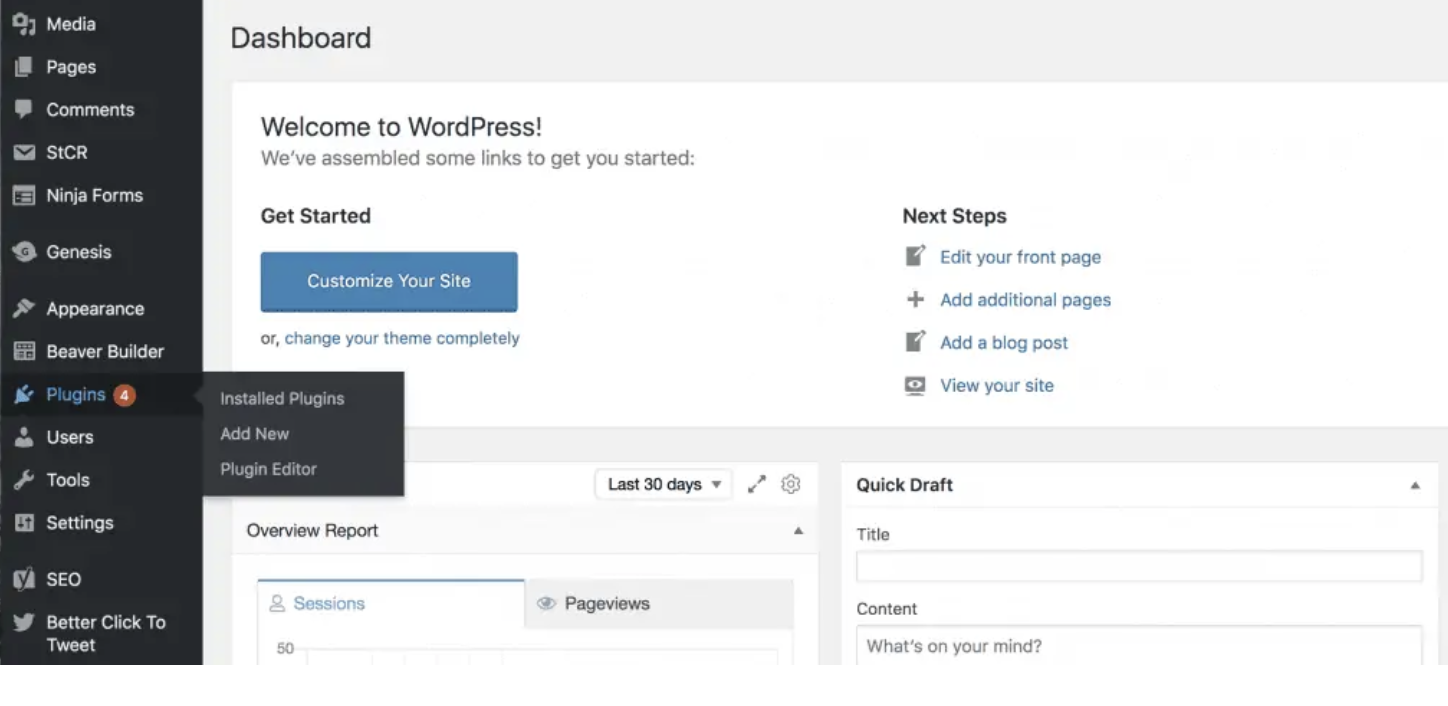
 SEO2 years ago
SEO2 years agoWordPress: How to Fix ‘Add New Plugin Menu Not Showing
-

 Digital Marketing1 year ago
Digital Marketing1 year ago13 Possible Reasons Why Your Google Ads Are Not Showing Up
-

 Software2 years ago
Software2 years agoWhy is Content Workflow Software Necessary for Content Production
-
TVs2 years ago
All You Need to Know About the Toman Tokyo Revengers