Best Picks
5 Digital Transformation & EdTech Trends: eLearning, Study Memberships & more

Is going to the college worth it as it enters its second wave of digital transformation? Are elearning and study memberships staying in 2023?
It’s the headline that keeps appearing in national and higher education articles. That’s because now more than half of Americans don’t believe that a college education is worthwhile financially. More institutions are taking up the task of measuring and articulating their worth as a result of dwindling enrolment and the mounting need to show a return on investment.
Tech skills on campus will be crucial in assessing ROI for students in the coming year and beyond and supporting schools and universities in their efforts to improve institutional performance. Colleges are gradually but surely arming themselves with the data and metrics they need to show their worth to stakeholders by utilizing new digital technologies and data-driven analytics.
Or, at the very least, they have started to research the tools and procedures they will need going ahead in order to be competitive and financially viable. Online and e-learning platforms are also adding their input to the cause at large. Study memberships happen to be a great chunk of the cause.
Adoption of Digital Technology
The adoption of digital technology is one of these tools and procedures, which helps to increase accessibility and affordability, student success results, digital credentials (CLR), improvements in finance and operations, and more. The important elements that support institutional success generally are also a part of the greater digital revolution (Dx) happening in the education sector at large.
The pandemic created so much disruption and upheaval in higher education, but it also served as a huge motivator for innovation, reviving interest in Dx. The initial wave of Dx was concentrated on important procedures that involved students. Major system and process changes in higher education were brought about by COVID and emergency remote instruction, which modernized long-standing procedures.
Important administrative procedures geared at institutional achievement are included in the second wave of Dx (not just digitizing old analog processes). Leading with a digital-first campus is the best way to align with institutional success in the now and the future.
Here are five Dx trends that the education sector should be aware of in 2023:
1) Data Analytics:
Institutional efficiency and advantage in the marketplace
Many initiatives for improvement are built on data analytics. For these endeavors, the institution as a whole needs robust, trustworthy, and easily available data. Money must be invested in this. A patchwork of systems and metrics is becoming a disadvantage for institutions, especially in light of the complexity of the business concerns facing higher education and the rising demand from important stakeholders for data-driven decision-making.
2) Online learning & Study Memberships: accessibility, affordability, and skill-based education
In addition to having access to online counseling and other social activities, college students are beginning to demand their institutions offer certain courses through online and/or hybrid learning, including tailored tutoring plans, – titled study memberships. Due to the growing popularity of online micro-credentials and study memberships that are less expensive and time-consuming, four-year schools will need to think about creating a blended offering that also proves the value of skills-based learning to employers. Given that more firms are removing the necessity for a college degree for job candidates, over 90% of HR professionals prefer alternative certifications that teach skills relevant to the workplace.
3) Modernizing credentials via the Comprehensive Learner Record (CLR)
In accordance with the aforementioned, universities are switching to digital and extended transcripts to more clearly show the return on investment of degrees. The following stage will go beyond the conventional course and grade transcript to offer a more practical type of digital credentials that is focused on accomplishments and learning based on abilities, such practices are possible under tailored study membership platforms. To showcase the breadth and depth of a student’s experience in academic and extracurricular activities, forward-thinking institutions like SolutionInn are experimenting with complete learner records.
4) Assessment automation: enhancing learning outcomes for students
More exacting assessment methods are necessary for compliance but can also be strategically utilized for ongoing development. Cycles between evaluation and improvement are shortened by automation of outcomes assessment collecting. For instance, it enables real-time access to data so that administrators can respond more quickly and frequently to make improvements in the classroom and intervene before students experience more serious complications. Traditionally, data would only be pulled once a year or once per term. It benefits staff accountability and operations as well as students.
5) Financial Intelligence: The finance department also needs innovation enhancements
The CFO has a duty to the board and other important stakeholders to provide trustworthy, pertinent financial data from which choices may be taken. Additionally, accreditation bodies are keeping a closer eye on things and raising the bar for financial accountability. The institution’s overall financial sustainability is improved by having tools for planning throughout the department and easily accessible automated financial data. In order to demonstrate their sustainable budgeting and ROI procedures, CFOs and business officers must have access to the necessary digital tools and processes.
Numerous schools, eLearning bodies, and universities are close to adopting and putting into practice the digital tools and procedures that characterize the second wave of Dx. The day when staying current with technology was only “good to have” is now over. Leaders in higher education, including SolutionInn, today are aware that advancing technology is essential to being competitive. They also realize that customized higher education technology capabilities provide the quickest, most dependable means to upgrade the entire campus, satisfy the needs of both students and parents, and demonstrate their value.
The pre-pandemic aversion to change is fading swiftly, while campuses will still move at their own speed (as they should) and budgets will vary significantly (as they do). Even if the implementation is years away, it’s crucial to be aware of what Dx options are now available and what is coming down the pipeline. A fantastic beginning on the correct path is keeping up with Dx advancements and creating a small list of high-impact areas of improvement on your learning journey.
Artifiсiаl Intelligenсe
Beyond Passwords: Your Digital Self in the Age of Blockchain (Clickbait: Ditch Passwords Forever! This Tech Will Secure Your Online Life)

Beyond Passwords: Your Digital Self in the Age of Blockchain (Clickbait: Ditch Passwords Forever! This Tech Will Secure Your Online Life)
Tired of password Purgatory? Enter the Blockchain Oasis.
Remember that frantic morning scramble, brain aching for the elusive password to your bank account?
Or the sinking feeling when “incorrect password” flashes back, mocking your best guess?
We’ve all been there, prisoners of our own digital fortresses, locked out by the very keys meant to protect us. But what if we told you there’s a better way, a passwordless paradise called blockchain technology?
Think of it as your digital Swiss bank account, secure and impregnable.
Unlike the flimsy walls of traditional passwords, easily breached by hackers and cracked by brute force, blockchain builds fortresses with ironclad cryptography.
Your data, from medical records to online purchases, isn’t hoarded by corporations or vulnerable to centralized attacks.
Instead, it lives on a distributed ledger, a communal vault encrypted across thousands of computers, each one a guardian vigilantly watching over your digital self.
This isn’t just about convenience (though ditching those sticky notes is a major perk!). This is about ownership and control.
Blockchain empowers you to be the gatekeeper of your digital life. You decide what information you share, with whom, and for how long.
No more Big Brother data slurping or shady companies monetizing your privacy. You become the sovereign ruler of your own digital kingdom, wielding the keys to unlock or deny entry.
Imagine accessing your healthcare records without divulging them to every hospital you visit.
Picture transferring money across borders, instantly and securely, without banks taking a hefty cut.
Envision a world where your online identity isn’t a mosaic scattered across corporate servers, but a unified passport you carry with pride, granting access to services based on your own terms.
This is the promise of blockchain: a future where security isn’t a fragile wall of passwords, but a vibrant ecosystem of trust and empowerment.
Are you ready to leave Password Purgatory behind and step into the Blockchain Oasis? Buckle up, savvy internet user, because the revolution has just begun.
The Downside of Traditional Passwords
Why Are Passwords Failing Us?
In our digital age, passwords are the guardians of our online identities, yet they are failing us in more ways than one. Despite being the first line of defense in digital security, traditional passwords are increasingly becoming the weakest link. Let’s explore why.
The Illusion of Strength in Complexity
Think of the last time you created a password. Chances are, you were prompted to include a mix of letters, numbers, and symbols – the more complex, the better, right?
However, this complexity often leads to passwords that are hard to remember and, ironically, not as secure as we think. Cybersecurity experts have long debunked the myth that complexity equates to security.
In reality, it’s the length and unpredictability of passwords that matter most. But even then, no password is impervious to the sophisticated tactics employed by hackers today.
The Human Factor: Password Fatigue and Security Risks
As humans, we have our limits in remembering complex strings of characters. This leads to password fatigue – the tendency to reuse passwords across multiple accounts for convenience.
It’s like using the same key for your house, car, and office; if one gets lost or stolen, everything is compromised. This common practice significantly heightens the risk of mass data breaches.
Once a hacker cracks one password, they potentially gain access to an entire suite of an individual’s personal and professional digital life.
The Hacker’s Playground: Vulnerabilities in Password-Based Security
Hackers have a plethora of tools at their disposal to breach password-protected accounts. Techniques like brute force attacks, where automated software tries countless combinations until it finds the right one, are surprisingly effective against weak passwords.
Phishing attacks, where users are tricked into revealing their passwords, are increasingly sophisticated and difficult to spot.
Even when we think our passwords are safely stored, large-scale data breaches at major companies reveal that this is not always the case.
The Cost of Password Management and Recovery
The administrative burden of managing and recovering passwords is another often-overlooked downside.
For businesses, the cost of resetting passwords and dealing with security breaches can be astronomical.
For individuals, the time and effort spent managing passwords, coupled with the anxiety of keeping them safe, are a significant mental burden.
Biometric Authentication: A Step Forward but Not a Panacea
The advent of biometric authentication – using fingerprints, facial recognition, or retinal scans – seemed like a promising solution.
However, while biometrics offer convenience, they are not without their flaws. Biometric data, once compromised, cannot be changed like a password.
There are also privacy concerns and the potential for misuse of biometric data by corporations or governments.
Looking Beyond Passwords: The Need for a Paradigm Shift
The limitations of traditional passwords highlight the need for a paradigm shift in digital security.
We need a solution that is both secure and user-friendly, something that doesn’t require us to remember complex strings of characters or put our personal biometrics at risk.
This is where blockchain technology comes into play, offering a new way to authenticate identities and secure data without the pitfalls of traditional passwords.
Conclusion
In conclusion, while passwords have been the cornerstone of digital security for decades, their numerous shortcomings are increasingly apparent in our connected world.
As cyber threats evolve, so must our approach to securing our digital lives.
The future of digital security lies in innovative technologies like blockchain, which promise to offer a more secure, efficient, and user-centric approach to protecting our digital identities.
Blockchain: The Game-Changer in Digital Security
How Does Blockchain Enhance Security?
In the digital world, where data breaches and cyber threats loom large, blockchain emerges as a beacon of hope, promising a more secure and trustworthy online environment.
But what exactly makes blockchain a game-changer in digital security? Let’s unpack this.
The Immutable Ledger: A Foundation of Trust
At its core, blockchain is a distributed ledger technology. Imagine a ledger that is not maintained by a single entity but is spread across a network of computers, each holding a copy of the ledger.
This decentralization is key to blockchain’s power. Once a record is added to the blockchain, altering it is next to impossible.
This immutability provides a foundation of trust and security unprecedented in digital transactions.
Decentralization: The Antidote to Centralized Risk
Centralization in traditional digital systems creates a single point of failure, a treasure trove for cybercriminals. Blockchain disrupts this by distributing data across a vast network, thereby diluting the risk.
Even if a part of the network is compromised, the rest remains unscathed, preserving the integrity of the entire system.
Cryptography: The Art of Secret Keeping
Blockchain employs advanced cryptography to secure the data.
Each block in the chain is secured with a cryptographic hash, a mathematical algorithm that turns data into a unique string of characters. Any change in the data alters the hash dramatically.
This means that tampering with a block would require altering all subsequent blocks, an almost Herculean task given the computational power required.
Transparency and Anonymity: A Balancing Act
Blockchain strikes a unique balance between transparency and anonymity.
While all transactions are visible to everyone in the network, the identities of the parties involved are protected.
This transparency ensures accountability and trust, while anonymity safeguards user privacy.
Smart Contracts: The Protocols of Trust
Smart contracts, self-executing contracts with the terms of the agreement directly written into code, are a revolutionary aspect of blockchain.
They automate and enforce contractual obligations, reducing the need for intermediaries and the risk of fraud or manipulation.
Beyond Cryptocurrency: Diverse Applications of Blockchain in Security
Blockchain’s potential extends far beyond the realms of cryptocurrency.
In digital identity verification, it offers a secure way to manage and authenticate identities without centralized databases.
In supply chain management, it ensures the authenticity and traceability of products. In voting systems, it can provide secure and transparent electoral processes.
Challenges in Blockchain Adoption
Despite its potential, blockchain’s adoption faces hurdles.
Scalability, energy consumption, and the integration with existing systems are significant challenges. Furthermore, regulatory uncertainties and a lack of widespread understanding of the technology hinder its broader acceptance.
Preparing for a Blockchain-Enabled Future
As we stand on the brink of a blockchain revolution in digital security, it’s essential to educate ourselves about this technology.
Businesses and individuals alike must stay informed about the latest developments in blockchain and explore how it can be integrated into their digital practices.
Conclusion
Blockchain technology offers a new paradigm in digital security, promising a more secure, transparent, and efficient way to safeguard digital assets and identities.
As we move forward, embracing this technology and overcoming its challenges will be key to building a safer digital world.

The Mechanics of Blockchain Security
Understanding the Nuts and Bolts
Blockchain security is often hailed as a groundbreaking innovation, but how does it really work? What makes it so secure and reliable?
Let’s dive into the mechanics of blockchain security and understand what sets it apart.
The Anatomy of a Blockchain
Picture a blockchain as a series of digital ‘blocks’ linked together in a chain.
Each block contains a set of transactions or data, securely encrypted.
Every time a new block is added, it is verified by multiple nodes (computers) in the network, making fraud or alteration extremely difficult.
The Power of Decentralization
Decentralization is the heartbeat of blockchain security.
Unlike traditional systems where data is stored on central servers, blockchain distributes data across a network of nodes.
This means there’s no single point of failure, making it incredibly resistant to cyber-attacks and data breaches.
Cryptography: The Backbone of Blockchain Security
Blockchain uses advanced cryptographic techniques. Each block contains a unique cryptographic hash of the previous block, creating a secure link.
Altering any information would change the hash, alerting the network to the tampering. This cryptographic chaining ensures the integrity and chronological order of the blockchain.
Consensus Protocols: Ensuring Network Agreement
Blockchain operates on consensus protocols, rules that dictate how transactions are verified and added to the block.
Popular protocols like Proof of Work (PoW) and Proof of Stake (PoS) ensure that all nodes in the network agree on the state of the ledger, preventing fraudulent transactions.
Smart Contracts: Automating Trust
Smart contracts on the blockchain automatically execute transactions when predetermined conditions are met.
These contracts run on code and eliminate the need for intermediaries, reducing the risk of manipulation and increasing efficiency.
Challenges and Limitations
Despite its strengths, blockchain isn’t without challenges.
Issues like scalability, energy consumption (especially with PoW), and integrating blockchain into existing systems remain significant hurdles.
There’s also the concern of ‘51% attacks’ in some blockchains, where if more than half the network’s computing power is controlled by one entity, they could potentially manipulate the network.
Conclusion
Blockchain security offers a robust and innovative approach to protecting digital information.
Its combination of decentralization, cryptography, and consensus protocols provides a level of security far beyond traditional methods.
As the technology matures and overcomes its current limitations, blockchain stands to revolutionize how we secure our digital world.
Blockchain vs. Passwords: A Comparative Analysis
Why Blockchain Wins
In the digital security arena, blockchain and traditional passwords represent two very different philosophies.
While passwords have been the cornerstone of digital security for decades, blockchain introduces a paradigm shift.
Let’s compare these two to understand why blockchain is emerging as the superior option.
Traditional Passwords: The Aging Security Guard
Think of traditional passwords as an aging security guard. They’ve been around for a long time, are familiar, but they’re not as effective as they used to be.
Passwords are vulnerable to a range of attacks – from brute force to phishing – and they rely heavily on human memory and behavior, which can be fallible.
Blockchain: The Digital Fort Knox
On the other hand, blockchain can be likened to a digital Fort Knox. It doesn’t rely on single-key entry like passwords.
Instead, it offers a distributed, immutable ledger with complex cryptographic techniques.
This makes blockchain inherently more secure, as altering any part of the chain would require an astronomical amount of computing power.
User Experience: Complexity vs. Simplicity
One of the biggest drawbacks of passwords is their complexity and the user fatigue they cause. In contrast, blockchain can streamline the user experience.
With blockchain, users can potentially have a single digital identity for multiple platforms, eliminating the need to remember numerous passwords.
Decentralization: Eliminating Single Points of Failure
Passwords often involve centralized databases, creating single points of failure. Blockchain distributes data across a vast network, significantly reducing this risk.
Even if a part of the network is compromised, the rest remains secure, safeguarding the overall integrity.
Recovery and Revocation: A Clear Winner
Losing a password can lead to a cumbersome recovery process. Blockchain offers a more resilient approach.
For instance, with decentralized identity solutions, users can recover their identity through distributed mechanisms, without relying on a central authority.
Scalability and Adoption Challenges
Despite its advantages, blockchain faces its own set of challenges, particularly in scalability and widespread adoption.
Integrating blockchain into existing systems and ensuring it can handle large volumes of transactions are areas that need addressing.
Conclusion
Comparing blockchain with traditional passwords illustrates why blockchain is poised to be the future of digital security.
Its decentralized nature, enhanced security features, and user-friendly potential make it a formidable tool against cyber threats.
As blockchain technology overcomes its current challenges, it could render traditional passwords obsolete, ushering in a new era of digital security.
Real-World Applications of Blockchain in Security
Blockchain in Action
The realm of blockchain extends far beyond the confines of cryptocurrency.
Its unique attributes are being harnessed in various sectors, revolutionizing the way we think about and implement digital security.
Let’s explore some of the most impactful real-world applications of blockchain technology.
Revolutionizing Digital Identity Verification
One of the most significant applications of blockchain is in digital identity verification.
Traditional methods of identity verification are fraught with risks – from data breaches to identity theft.
Blockchain introduces a decentralized approach, where users can control their digital identities without relying on a central authority. This method not only enhances security but also offers greater privacy and control to individuals.
Transforming Supply Chain Management
In supply chain management, blockchain is a game-changer.
It provides a transparent and tamper-proof record of transactions and movements of goods.
This transparency ensures the authenticity of products, combats counterfeit goods, and enhances trust among consumers and businesses alike. From farm to table or manufacturer to retailer, every step is verifiable and secure.
Secure Voting Systems
Blockchain is making strides in securing electoral processes.
By leveraging blockchain, voting systems can become more secure, transparent, and resistant to tampering. This application could revolutionize democracy, making elections more accessible and trustworthy.
Healthcare Data Management
In healthcare, blockchain can securely manage patient records, ensuring privacy and data integrity.
It provides a secure platform for sharing medical records between authorized individuals and institutions, improving the efficiency and accuracy of diagnoses and treatments.
Challenges and Considerations
While these applications are promising, challenges such as scalability, regulatory compliance, and integration with existing systems remain.
There is also a need for a broader understanding and acceptance of blockchain technology among the general public and within specific industries.
Conclusion
The real-world applications of blockchain in security demonstrate its potential to revolutionize how we manage and protect digital information.
As the technology evolves and these challenges are addressed, blockchain is set to play a pivotal role in shaping a more secure and efficient digital world.
Overcoming the Challenges of Implementing Blockchain
Tackling the Obstacles
Blockchain technology, despite its potential, is not without its challenges.
Implementing blockchain in existing systems and processes requires navigating a complex landscape of technical, regulatory, and practical hurdles.
Let’s delve into these challenges and explore how they can be overcome.
Scalability: The Growing Pains of Blockchain
One of the primary challenges facing blockchain is scalability.
As the number of transactions on a blockchain increases, so does the need for greater computational power and storage.
This can lead to slower transaction times and higher costs, making it less practical for large-scale applications.
Solutions like sharding, where the blockchain is divided into smaller, more manageable pieces, and layer 2 solutions that process transactions off the main chain, are being explored to address this issue.
Energy Consumption: A Sustainable Dilemma
Blockchain, especially those using Proof of Work (PoW) consensus mechanisms, can be energy-intensive.
This raises concerns about the environmental impact of blockchain technologies.
Transitioning to more energy-efficient consensus mechanisms like Proof of Stake (PoS) or exploring renewable energy sources for mining operations are ways to mitigate this issue.
Regulatory Hurdles: Navigating the Legal Landscape
The decentralized and often borderless nature of blockchain poses significant regulatory challenges. Different countries have varying regulations regarding digital transactions, data privacy, and cryptocurrency.
Ensuring compliance while fostering innovation requires a delicate balance and ongoing dialogue between technology providers, users, and regulatory bodies.
Integration with Existing Systems
Integrating blockchain technology with existing digital infrastructures can be complex. Compatibility issues, the need for technical expertise, and the disruption of established processes can pose significant barriers.
Developing user-friendly blockchain solutions and providing education and training can facilitate smoother integration.
Security Concerns: Addressing Vulnerabilities
While blockchain is inherently secure, it is not immune to risks.
Potential security issues, such as 51% attacks, smart contract vulnerabilities, and key management challenges, need to be addressed.
Continuous research and development, alongside robust security protocols, are essential to bolster blockchain security.
Conclusion
Overcoming the challenges of implementing blockchain is crucial for realizing its full potential.
This involves addressing scalability and energy consumption issues, navigating regulatory landscapes, integrating with existing systems, and bolstering security measures.
As we tackle these obstacles, blockchain’s promise in transforming digital security becomes increasingly attainable.
The Future of Blockchain in Personal Security
What Lies Ahead
The horizon of personal security is being redrawn by blockchain technology.
As we edge further into the digital era, blockchain is poised to play a critical role in shaping our digital identities and safeguarding our online activities.
Let’s explore the promising future of blockchain in personal security.
Blockchain as a Guardian of Digital Identities
Imagine a world where your digital identity is as unique and unforgeable as your DNA.
Blockchain makes this possible. With its ability to create tamper-proof digital identities, blockchain is setting the stage for a future where identity theft and fraud become relics of the past.
These blockchain-based identities could replace traditional login credentials, offering a more secure and convenient way to access online services.
Enhanced Privacy and Control Over Personal Data
In an age where data breaches are commonplace, blockchain offers a beacon of hope. It empowers individuals with greater control over their personal data.
Instead of entrusting personal information to multiple organizations, blockchain allows individuals to store their data securely and share it selectively, using cryptographic keys.
Decentralized Finance (DeFi) and Personal Wealth Management
The rise of decentralized finance (DeFi) is another area where blockchain is set to transform personal security. By removing intermediaries, DeFi platforms offer more control and security over personal financial transactions.
Blockchain’s transparency and security features make it an ideal backbone for these platforms, promising a more secure and equitable financial ecosystem.
Challenges and Opportunities in Personal Security
The journey towards a blockchain-powered future is not without challenges.
Issues like public acceptance, technological literacy, and regulatory frameworks need to be addressed.
However, these challenges also present opportunities for innovation, collaboration, and education in the realm of personal security.
Conclusion
As blockchain technology matures, its potential to redefine personal security is immense.
From securing digital identities to revolutionizing personal finance, blockchain stands as a pillar of trust and security in the digital world.
Embracing this technology could lead us to a future where our digital lives are more secure, private, and under our control.
How to Prepare for the Blockchain Revolution
Getting Ready for Change
The blockchain revolution is not just coming; it’s already here. But how do we prepare for this seismic shift in digital security?
Whether you’re an individual, a business leader, or a technology enthusiast, gearing up for the blockchain era requires a proactive approach. Here’s how to get ready.
Educating Yourself and Your Team
Knowledge is power, especially when it comes to emerging technologies. Start by educating yourself about blockchain technology.
Online courses, webinars, and industry conferences are great resources. If you’re leading a team or an organization, consider facilitating blockchain training sessions to stay ahead of the curve.
Evaluating Blockchain Applications in Your Life or Business
Look at how blockchain could apply to your personal life or your business operations.
This might involve exploring blockchain-based solutions for data storage, identity verification, or even investment opportunities in the blockchain space.
Participating in Blockchain Communities and Networks
Engagement with blockchain communities can provide invaluable insights and keep you updated on the latest trends and developments.
Online forums, social media groups, and local meetups can serve as platforms for discussion and networking.
Experimenting with Blockchain Technologies
Hands-on experience is one of the best ways to understand blockchain.
Consider experimenting with blockchain applications, such as using a blockchain-based service or investing in cryptocurrencies.
This practical exposure can demystify the technology and reveal its potential applications in your life.
Understanding the Regulatory Landscape
Stay informed about the regulatory environment surrounding blockchain technology, especially if you’re considering it for business applications.
Keeping abreast of legal and compliance issues is crucial to navigating the blockchain space successfully.
Conclusion
Preparing for the blockchain revolution involves education, experimentation, and engagement with the blockchain community.
By taking these steps, individuals and businesses can position themselves to harness the benefits of blockchain technology and navigate the challenges it presents.
The future belongs to those who are ready to embrace change and innovate, and blockchain is a field ripe with opportunities for both.
Debunking Myths about Blockchain Security
Separating Fact from Fiction
Blockchain technology, while revolutionary, is often shrouded in myths and misconceptions, especially regarding its security aspects.
It’s crucial to separate fact from fiction to understand the true capabilities and limitations of blockchain security. Let’s debunk some common myths.
Myth 1: Blockchain is Inherently Invulnerable
Fact: While blockchain’s design makes it highly secure, it’s not infallible. Issues like code vulnerabilities in smart contracts and potential 51% attacks on certain types of blockchains can pose risks.
However, compared to traditional databases, blockchain’s decentralized and cryptographic nature makes it significantly more secure against common cyber threats.
Myth 2: All Blockchains are Public and Transparent
Fact: Not all blockchains are created equal.
While public blockchains offer transparency and decentralization, private blockchains control access more strictly, offering privacy and efficiency.
The choice between public and private blockchains depends on the specific needs and context of use.
Myth 3: Blockchain and Cryptocurrency are Interchangeable
Fact: Cryptocurrencies like Bitcoin are just one application of blockchain technology.
Blockchain has a myriad of other applications beyond digital currencies, from supply chain management to digital identity verification.
Myth 4: Blockchain Transactions are Always Anonymous
Fact: Anonymity in blockchain transactions varies. While cryptocurrencies like Bitcoin offer a degree of anonymity, other blockchains provide full transparency.
Moreover, advanced techniques can sometimes trace blockchain transactions, challenging the notion of absolute anonymity.
Myth 5: Blockchain is a Data Privacy Solution
Fact: Blockchain can enhance data security, but it doesn’t automatically guarantee data privacy.
The way data is recorded and encrypted on the blockchain plays a crucial role in determining privacy levels.
Conclusion
Understanding the realities of blockchain security is vital for its effective implementation and trust.
By debunking these myths, we can appreciate the true potential and limitations of blockchain, paving the way for informed and effective use of this transformative technology.
The Ultimate Guide to Blockchain Security Tools
Your Toolkit for the Future
As blockchain technology becomes increasingly prevalent, the importance of understanding and utilizing blockchain security tools grows.
Whether you’re a blockchain enthusiast, a business professional, or someone curious about the technology, having a grasp of these tools is essential.
Here’s a guide to some key blockchain security tools.
Cryptographic Wallets: Secure Storage for Digital Assets
Cryptographic wallets are essential for securely storing and managing digital assets like cryptocurrencies.
They use private keys, a form of cryptography, to enable users to access and transact their assets securely.
Choosing a reputable wallet, whether it’s a software, hardware, or paper wallet, is crucial for asset security.
Smart Contract Auditing Tools
As smart contracts become more complex, the need for thorough auditing increases.
Tools like Mythril and OpenZeppelin provide security analysis of smart contracts, identifying vulnerabilities and ensuring that they behave as intended.
Blockchain Explorers: Tracking Transactions
Blockchain explorers are tools that allow users to view and track transactions on a blockchain.
They offer transparency and the ability to verify transactions, which is crucial for trust and security in blockchain ecosystems.
Decentralized Identity Applications
Decentralized identity applications use blockchain to provide users with more control over their personal information.
These tools are foundational for creating secure digital identities and can be used for authentication purposes without the need for centralized databases.
API Security Tools
APIs are vital for blockchain applications, and securing them is paramount.
Tools like OAuth 2.0, OpenID Connect, and API gateways help secure and manage access to blockchain-based APIs, protecting against unauthorized access and data breaches.
Conclusion
The landscape of blockchain security tools is vast and evolving. Familiarizing oneself with these tools is a step towards harnessing the full potential of blockchain technology.
As blockchain continues to grow and integrate into various sectors, these tools will become instrumental in securing and optimizing blockchain applications.
Final Conclusion
As we journey through the intricate world of blockchain technology and its impact on digital security, it becomes evident that we are standing on the brink of a major technological revolution.
From debunking myths about blockchain security to exploring an array of advanced security tools, our expedition reveals a future where blockchain is poised to redefine the norms of digital safety and privacy.
This transformative technology, with its decentralized nature, cryptographic security, and innovative applications, offers more than just a new way to secure digital transactions; it promises a future where our digital identities and assets are protected with unprecedented robustness.
Embracing blockchain, understanding its potential, and preparing for its widespread adoption are crucial steps towards a safer, more secure digital world.
As we continue to explore and innovate in this exciting field, the possibilities for enhanced digital security seem limitless.
FAQs
Is blockchain technology applicable in everyday life, or is it just for tech experts?
Blockchain technology is increasingly becoming applicable in everyday life, not just for tech experts. Its applications range from secure online transactions and digital identity management to supply chain tracking and voting systems, making it relevant and beneficial for the general public.
Can blockchain be used to secure all kinds of digital data, or is it limited to financial transactions?
Blockchain can secure various kinds of digital data, not just financial transactions. Its applications include securing personal data, healthcare records, digital identities, and more, demonstrating its versatility beyond just financial uses.
How does blockchain technology offer more security compared to traditional security methods?
Blockchain technology offers more security through its decentralized structure, which eliminates single points of failure, and its use of advanced cryptography, which ensures data integrity and prevents unauthorized alterations.
Are there any significant environmental concerns associated with blockchain technology?
Yes, certain blockchain implementations, particularly those using Proof of Work (PoW) consensus mechanisms, can be energy-intensive and raise environmental concerns. However, newer technologies like Proof of Stake (PoS) are more energy-efficient and are being adopted to address these concerns.
How can individuals ensure they are using blockchain technology safely and effectively?
Individuals can ensure safe and effective use of blockchain technology by educating themselves about its basics, using reputable blockchain services and wallets, staying informed about security best practices, and being cautious of scams and fraudulent schemes in the blockchain space.
Verified Source References
- Blockchain Technology Fundamentals: IBM Blockchain Essentials
- Understanding Cryptographic Wallets: Investopedia – Cryptocurrency Wallets
- Guide to Smart Contract Auditing Tools: Ethereum Smart Contract Best Practices
- Blockchain Explorers and Their Use: Blockgeeks – Blockchain Explorers
- Decentralized Identity Applications in Blockchain: Decentralized Identity Foundation
Best Picks
Deep Learning Demystified: How Neural Networks Work (Without the Geek Speak)

Deep Learning Demystified: How Neural Networks Work (Without the Geek Speak)
Ever heard the term “deep learning” and felt your eyes glaze over? You’re not alone.
This complex field of Artificial Intelligence (AI) often gets shrouded in jargon and technical mumbo jumbo, leaving the rest of us mortals feeling like we’re peering through a keyhole at a secret society of code-slinging sorcerers.
But fear not, fellow curious minds! Today, we’re embarking on a journey to demystify deep learning.
We’ll ditch the dense equations and ditch the dry academic lingo, and instead, crack open the hood of these neural networks and see how they tick… in plain English, of course.
Imagine this: You’re a detective trying to solve a case based on a blurry photo. You squint, analyze, compare details, and slowly, a picture starts to form.
Deep learning works in a similar way, except instead of blurry photos, it deals with mountains of data. And instead of your detective instincts, it uses a network of interconnected processors called artificial neurons to sift through that data, identify patterns, and make sense of it all.
Think of each neuron as a tiny detective.
It receives information from its neighbors, analyzes it based on its own internal “weightings,” and then fires off a signal if it finds something interesting.
This signal then ripples through the network, with each neuron influencing its neighbors, refining the understanding as it travels. It’s like a giant game of telephone, but instead of gossip, it’s churning out insights and predictions.
So, what kind of cases can these AI detectives tackle?
The possibilities are endless! From recognizing faces in photos to predicting stock market trends, from translating languages to writing poetry, deep learning is transforming how we interact with technology and the world around us.
But before we get too carried away with the hype, let’s acknowledge the elephant in the room: deep learning isn’t magic.
It’s a powerful tool, but it’s not a one-size-fits-all solution. It requires massive amounts of data, skilled programmers, and hefty computational resources. And like any tool, it can be misused, leading to biases and ethical concerns.
That’s why understanding how deep learning works is crucial.
It’s not just about appeasing our inner geek (although, let’s be honest, that’s pretty cool too!). It’s about being informed citizens in an AI-driven world.
It’s about knowing when to trust these digital detectives and when to question their methods.
So, buckle up, fellow knowledge seekers! This journey into the world of deep learning is just getting started.
In the coming sections, we’ll delve deeper into the inner workings of these neural networks, explore different types of deep learning architectures, and even get our hands dirty with some practical applications.
Get ready to:
- Unravel the mysteries of backpropagation: the algorithm that trains these AI detectives.
- Meet the heavy hitters of deep learning: Convolutional Neural Networks (CNNs), Recurrent Neural Networks (RNNs), and more!
- Witness the power of deep learning in action: from self-driving cars to medical diagnosis.
- Grapple with the ethical considerations: bias, fairness, and the future of AI.
By the end of this adventure, you’ll no longer be intimidated by the term “deep learning.”
You’ll be able to hold your own in any AI conversation, impress your friends with your newfound knowledge, and maybe even start building your own tiny neural network detective!
Are you ready to crack the code? Let’s begin!
Unraveling the Mystery of Backpropagation: How AI Detectives Learn
Remember our detective analogy? Imagine they’re investigating a crime scene, but they don’t have a clear picture of the culprit.
That’s where backpropagation comes in. It’s like a feedback loop that helps these AI sleuths adjust their weights and refine their understanding based on the results they get.
Think of it like this:
- The detectives (neurons) fire off signals based on their current weights.
- Those signals reach the “output layer” and produce a prediction or decision.
- The prediction is compared to the actual outcome (the “ground truth”).
- If the prediction is wrong, the error is calculated.
- The error is then backpropagated through the network, layer by layer.
- At each layer, the weights are adjusted based on the error signal.
- This process repeats until the network gets better at making accurate predictions.
It’s like a game of hot and cold, where the AI detectives get warmer (closer to the correct answer) with each iteration of backpropagation.
The more data they process, the finer their weights become, and the better they become at solving their “cases.”
Backpropagation is the engine that drives deep learning.
It’s what allows these complex networks to learn from their mistakes and improve over time.
It’s not always a smooth ride – sometimes the detectives get stuck in dead ends or local minima (think of it as a logic trap). But with careful tuning and optimization techniques, they can eventually find their way to the right solution.
Mastering backpropagation might seem daunting, but understanding its basic principles is essential for appreciating the power and limitations of deep learning.
It’s like knowing the rules of chess before you can truly appreciate the brilliance of a grandmaster’s moves.
Now, let’s meet some of the key players in the deep learning world…
The A-Team of Deep Learning: Meet the Network Architectures
Just like any detective agency has its own team of specialists, deep learning boasts a diverse lineup of network architectures, each suited for different tasks. Here are some of the most renowned:
-
Convolutional Neural Networks (CNNs): These are the visual superstars, adept at recognizing patterns in images and videos. Think of them as detectives with eagle eyes, scrutinizing every pixel to identify objects, faces, and even emotions. CNNs are the driving force behind self-driving cars, facial recognition software, and image classification algorithms.
-
Recurrent Neural Networks (RNNs): These are the memory masters, able to process sequences of data like text, speech, and music. Imagine them as detectives with a keen ear for detail, piecing together clues from past events to predict what might happen next. RNNs power machine translation, voice assistants, and even music generation algorithms.
-
Generative Adversarial Networks (GANs): These are the creative geniuses, capable of generating new data that mimics real-world examples. Think of them as two rival detective teams, one trying to create convincing forgeries and the other trying to expose them. This constant competition pushes both teams to improve, resulting in incredibly realistic images, videos, and even music.
These are just a few examples, and the world of deep learning architectures is constantly evolving.
But by understanding the strengths and weaknesses of these key players, you’ll be well-equipped to navigate the ever-expanding landscape of AI.
Stay tuned, as we delve deeper into the real-world applications of these powerful tools and explore the ethical considerations that come with their growing influence.
Witnessing the Power of Deep Learning: From Self-Driving Cars to Medical Miracles
We’ve explored the inner workings of deep learning and met the star players in the field. Now, let’s step outside the lab and witness these AI detectives in action, solving real-world problems and making a tangible impact on our lives.
Self-Driving Cars: Navigating the Road to the Future
Imagine a world where traffic jams are a distant memory, accidents are drastically reduced, and everyone can enjoy a relaxed ride without the stress of driving.
This isn’t science fiction; it’s the near future powered by deep learning.
Convolutional Neural Networks, trained on massive datasets of images and sensor data, are the brains behind self-driving cars.
They’re constantly learning to perceive their surroundings, identify objects, and make split-second decisions to navigate roads safely.
As these systems continue to evolve, they hold the potential to revolutionize transportation, making our roads safer, more efficient, and accessible to everyone.
Medical Diagnosis: Deep Learning Aids the Doctor’s Intuition
From analyzing X-rays and MRIs to detecting cancers in their earliest stages, deep learning is transforming the field of medicine.
By sifting through vast amounts of medical data, AI algorithms can identify subtle patterns and abnormalities that might escape the human eye.
This doesn’t replace the doctor’s expertise, but rather acts as a powerful tool to enhance their diagnostic accuracy and provide valuable insights for personalized treatment plans.
Imagine a scenario where a doctor receives a patient’s scan and, within seconds, a deep learning system flags a potential tumor with 99% accuracy.
This early detection can be life-saving, allowing for prompt intervention and better chances of successful treatment.
Language Translation: Breaking Down the Barriers of Communication
The world is becoming increasingly interconnected, and the ability to communicate across languages is more important than ever.
Here, too, deep learning plays a crucial role. Recurrent Neural Networks are trained on vast amounts of translated text, learning the nuances of different languages and developing the ability to translate with impressive accuracy and fluency.
This technology is breaking down communication barriers, enabling real-time conversations between people who speak different languages.
It’s revolutionizing business, education, and travel, fostering a more connected and inclusive global community.
These are just a few examples of how deep learning is transforming our world.
From tackling climate change to predicting natural disasters, the applications are endless. But with any powerful tool comes the responsibility to use it ethically and responsibly.
Navigating the Ethical Maze: Deep Learning and the Responsibility We Share
As deep learning becomes more sophisticated and integrated into our lives, ethical considerations come to the forefront.
Bias in training data can lead to discriminatory algorithms, privacy concerns arise with the collection and analysis of vast amounts of personal data, and the potential for misuse of AI for malicious purposes cannot be ignored.
It’s our collective responsibility to ensure that deep learning is developed and deployed ethically. We need to:
- Promote diversity and inclusion in the field of AI to mitigate bias in algorithms and ensure fairer outcomes for all.
- Establish clear guidelines and regulations for data collection, storage, and usage to protect individual privacy and prevent misuse.
- Engage in open dialogue and public education about the capabilities and limitations of AI to foster transparency and trust.
By embracing these principles, we can harness the power of deep learning for good, ensuring that it serves humanity and enhances our lives in a responsible and equitable manner.
Frequently Asked Questions about Deep Learning
Can deep learning replace human intelligence?
While deep learning is incredibly powerful, it’s not designed to replace human intelligence. Instead, it excels at tasks that require pattern recognition and large-scale data analysis, complementing and augmenting human capabilities.
Is deep learning dangerous?
Like any powerful tool, deep learning can be misused if not developed and deployed responsibly. It’s crucial to address ethical concerns and implement safeguards to ensure AI serves humanity for good.
Will deep learning take away my job?
While some jobs may be impacted by automation, deep learning is also creating new opportunities in fields like AI development, data science, and cybersecurity. Adapting to the changing landscape and continuously learning new skills will be key to thriving in the AI-powered future.
Can I learn deep learning myself?
Absolutely! There are numerous online resources, tutorials, and even introductory courses available to help you understand the basics of deep learning. While mastering the field requires dedication and advanced skills, gaining a foundational understanding is within reach for anyone with curiosity and a passion for learning.
What is the future of deep learning?
The future of deep learning is brimming with possibilities. From personalized medicine and advanced robotics to intelligent cities and climate change solutions, the potential applications are vast and exciting. We are on the cusp of a new era
Beyond the Hype: Demystifying the Myths and Misconceptions of Deep Learning
Deep learning, with its mind-bending abilities and transformative potential, often gets shrouded in a fog of sensationalism and misconceptions.
But it’s crucial to remember that beneath the hype lies a powerful tool, and like any tool, it needs to be understood and wielded responsibly.
Let’s dispel some of the common myths surrounding deep learning:
Myth #1: Deep learning is magic.
Reality: While deep learning’s achievements are impressive, it’s not magic.
It’s a rigorous mathematical framework built on layers of algorithms and trained on massive amounts of data.
Understanding its core principles and limitations is essential for discerning the genuine potential from the overhyped promises.
Myth #2: Deep learning will replace humans.
Reality: Deep learning excels at specific tasks, particularly those involving data analysis and pattern recognition.
However, it lacks the creativity, adaptability, and critical thinking skills that define human intelligence.
We’re likely to see a future where humans and AI collaborate, each leveraging their strengths for synergistic outcomes.
Myth #3: Deep learning is a black box.
Reality: While the complexity of deep learning models can be daunting, they’re not entirely opaque.
Techniques like explainable AI (XAI) are enabling us to understand how these models arrive at their decisions, increasing transparency and fostering trust.
Myth #4: Deep learning is only for the tech giants.
Reality: The democratization of technology is making deep learning increasingly accessible.
Open-source tools, cloud platforms, and educational resources are empowering individuals and small businesses to leverage this technology for their own endeavors.
Myth #5: Deep learning is inherently biased.
Reality: Biases are often introduced into deep learning models by the data they’re trained on.
Therefore, it’s crucial to ensure diversity and inclusion in data collection and algorithm development to mitigate bias and promote fairness in AI applications.
By demystifying these myths, we can foster a more informed and balanced conversation about deep learning.
Recognizing its potential while acknowledging its limitations and potential pitfalls is key to harnessing this powerful technology for the betterment of humanity.
The Enduring Quest: A Deep Learning Journey Just Begins
Our journey into the fascinating world of deep learning has just begun.
We’ve explored its inner workings, witnessed its applications, and grappled with its ethical considerations. But this is by no means an exhaustive exploration.
As this field continues to evolve at breakneck speed, our collective learning journey must keep pace.
Remember, true understanding doesn’t lie in passively consuming information. It lies in actively questioning, exploring, and engaging in critical discourse.
So, continue to ask questions, delve deeper into the topics that spark your curiosity, and participate in shaping the future of AI responsibly.
The next chapter of deep learning is yet to be written, and each of us has the potential to become its co-author.
Let’s embrace the power of curiosity, collaboration, and ethical responsibility to ensure that this powerful technology serves as a force for good in the world.
The journey isn’t just about understanding deep learning; it’s about shaping its future. Are you ready to be part of it?
Best Picks
The Best Way to Choose a Gun Cleaning Kit

If you own a gun, then investing in a gun cleaning kit is a must. A gun cleaning kit is essential for proper maintenance of your firearm. But, with so many different gun cleaning kits out there, it can be hard to know which one is best for you and your gun. In this blog post, we’ll explore the best way to choose a gun cleaning kit for your AR rifle or pistol.
Decide What You Need
When you’re looking for the right gun cleaning kit for your AR rifle or pistol, it’s important to decide what you need. Every gun is different and may require different supplies, so you’ll want to make sure you get a gun cleaning kit that includes everything you need to properly clean and maintain your gun. GunBuilders.com has a great selection of gun cleaning kits, including everything from basic kits to advanced kits that include all the necessary components and tools. With the right kit, you can ensure that your gun stays in top condition.
Consider the Quality
When shopping for a gun cleaning kit, you want to make sure that you get a quality product. Quality gun cleaning kits will last longer, offer more features, and will provide you with a better overall experience. GunBuilders.com is one of the best resources to find high-quality gun cleaning kits for your AR rifle or pistol. They carry top brands like Otis, Hoppe’s, and Butch’s that are known for their durability and dependability.
When selecting a gun cleaning kit, look for ones that include the necessary components like rods, brushes, jags, mops, and cleaning solvents. Make sure that all of the components are well made and easy to use. Read reviews on GunBuilders.com and compare the different kits to find one that offers the best quality for your needs. It is important to invest in a good quality gun cleaning kit because it will save you money in the long run.
Compare the Prices
When it comes to selecting the right gun cleaning kit for your AR rifle or pistol, one of the most important factors to consider is price. It’s essential to compare the prices of the different kits available on the market, as the cost of a kit can vary significantly from one brand to the next. You should also consider the quality of the components included in the kit, as well as any extras such as cleaning rods, patches, and brushes.
Start by making a list of your preferred gun cleaning kit brands and researching the cost of their offerings. Consider both the upfront cost of the kit as well as any additional costs that may be associated with use, such as replacement parts or specialty cleaning solutions. You should also look at the cost of purchasing individual components from each brand in case you need to replace an item down the line.
It’s important to remember that while a higher price tag may indicate better quality, this isn’t always the case. Look for deals and promotions, as well as customer reviews, to get an idea of which kits offer the best value for money. This will help you make an informed decision when it comes time to buy a gun cleaning kit.
Check the Reviews
When shopping for a gun cleaning kit, it’s important to read reviews from other gun owners and experts. You can find reviews on websites such as GunCritic or Guns & Ammo Magazine. Reading reviews can help you identify the best gun cleaning kits based on quality, price, and customer satisfaction.
You should also consider checking out any user forums related to the type of gun cleaning kit you’re interested in. Here, you can ask questions about the product, compare different brands and models, and get honest feedback from people who have actually used the kit.
Finally, if you know someone who has recently bought a gun cleaning kit, ask them for their opinion. Getting a first-hand recommendation from someone you trust can be a great way to ensure that you’re investing in a high-quality gun cleaning kit that meets your needs.
-

 Education2 years ago
Education2 years agoCreating Engaging And Relevant Content As A Literacy Influencer
-

 Internet3 years ago
Internet3 years agoWhat Are the Differences Between WP Rocket, RocketCDN and Cloudflare
-

 How To..3 years ago
How To..3 years agoWhat Is Better Than Safety Deposit Box
-

 Mobile Phones3 years ago
Mobile Phones3 years agoKnow About the New Upcoming Mobile Phones
-
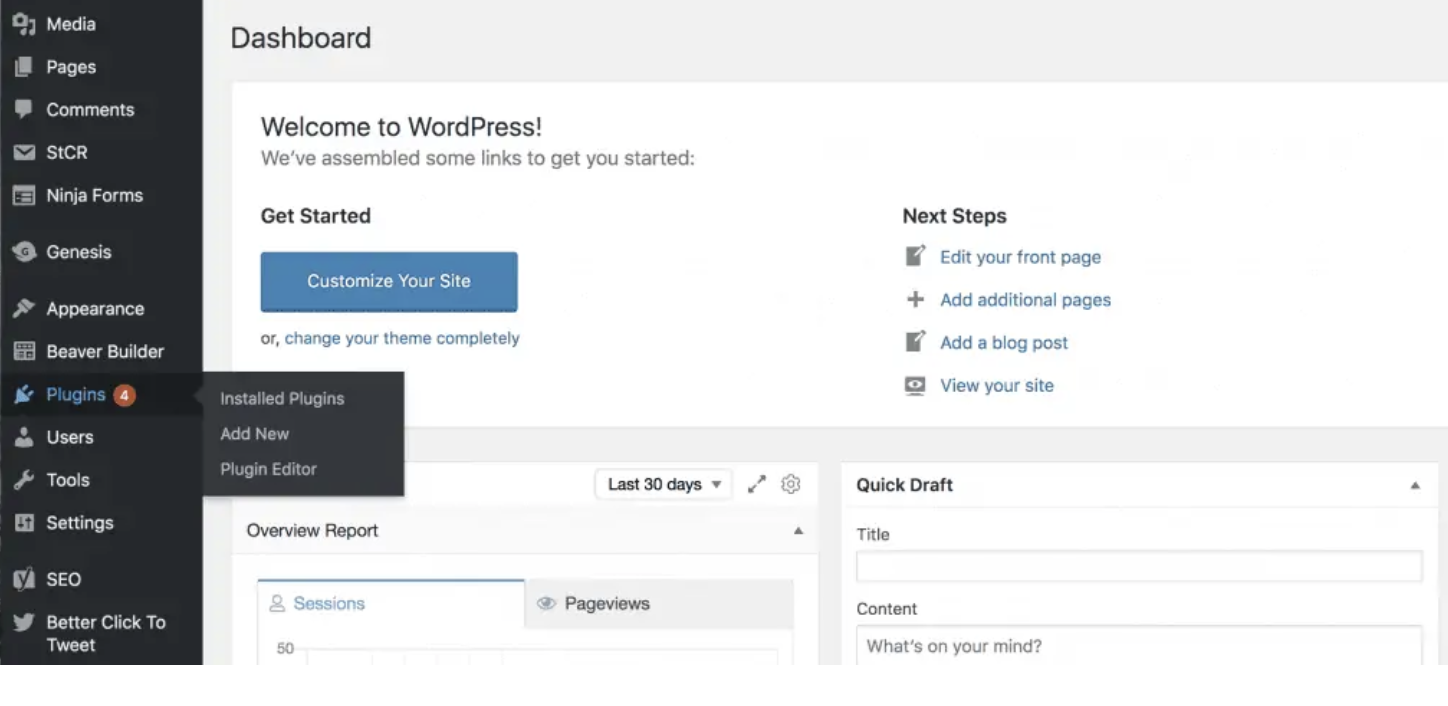
 SEO2 years ago
SEO2 years agoWordPress: How to Fix ‘Add New Plugin Menu Not Showing
-

 Software2 years ago
Software2 years agoWhy is Content Workflow Software Necessary for Content Production
-

 Digital Marketing1 year ago
Digital Marketing1 year ago13 Possible Reasons Why Your Google Ads Are Not Showing Up
-
TVs2 years ago
All You Need to Know About the Toman Tokyo Revengers